LetsDefend - SOC326
Impersonating Domain MX Record Change Detected
Initial incident
We start by seeing the initial incident
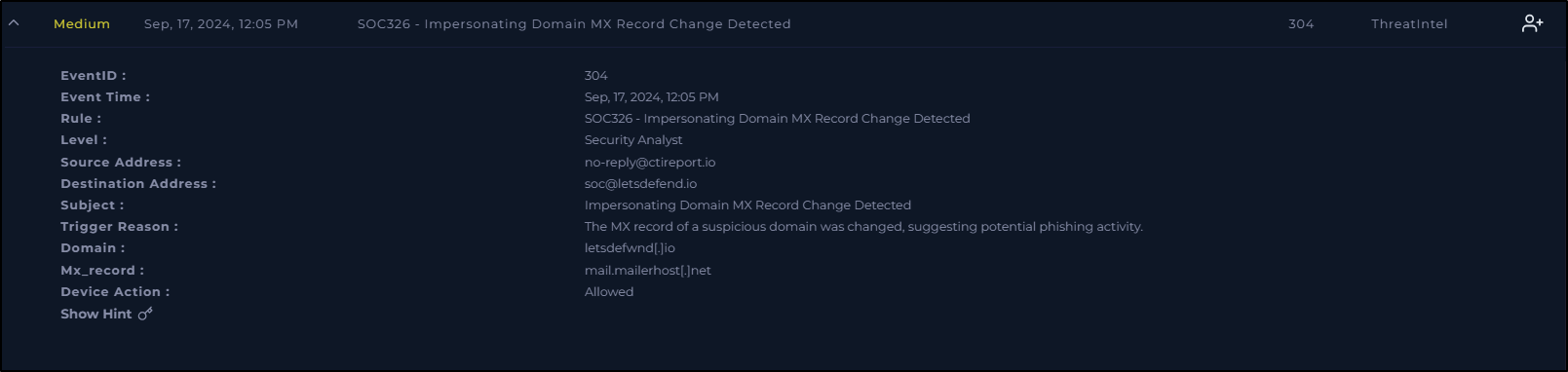
A Medium severity incident is reported on Sep 17th 2024 at 12:05 PM
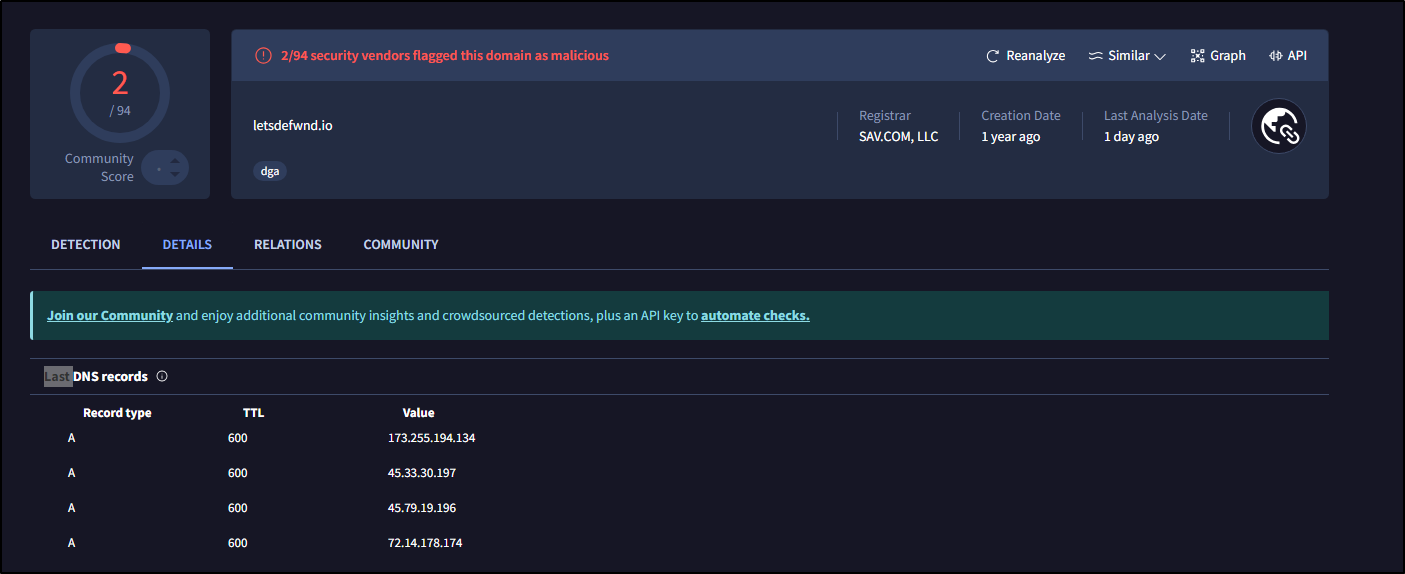
An alert was triggered due to a suspicious Mail Exchange (MX) record modification, involving a domain that bears a striking resemblance to letsdefend.io, with a substitute variation letsdefwnd.io. This clearly bears the hallmarks of a phishing attack, where a treat actor has intentionally crafted a malicious domain with the aim of deceiving unsuspecting individuals
An MX record is a type of DNS record that identifies the mail servers authorized to receive emails on behalf of the domain
The source address for the alert is no-reply@ctireport.io, which is likely associated with a threat intelligence provider (such as CrowdStrike Falcon, Cisco Talos, etc.). These providers monitor public data sources, including domains and DNS records, for changes that might indicate potential phishing attempts or other malicious activities
Understanding the attack process
- Register a domain that closely resembles ours
letsdefwnd.io - Change the MX record of the impersonating domain letsdefwnd.io to point to their mail server
mail.mailerhost.net. This change will allow them to receive and manage all emails directed to the lookalike domain - Send phishing emails from the impersonating domain
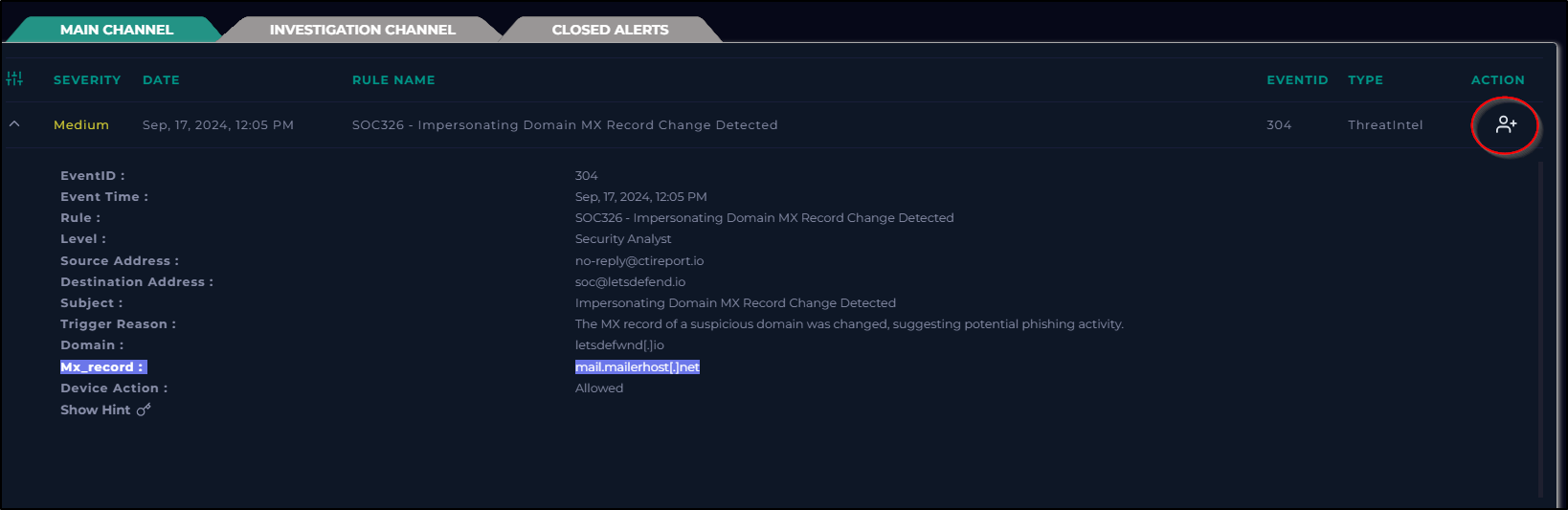
Let’s take ownership of the alert
Great, now that we have ownership the alert will be in our Investigation Channel
Now, we can begin investigation. Since this is clearly a malicious domain intended to phish emails, let’s head over the the Email Security Tab to look for any phishing emails
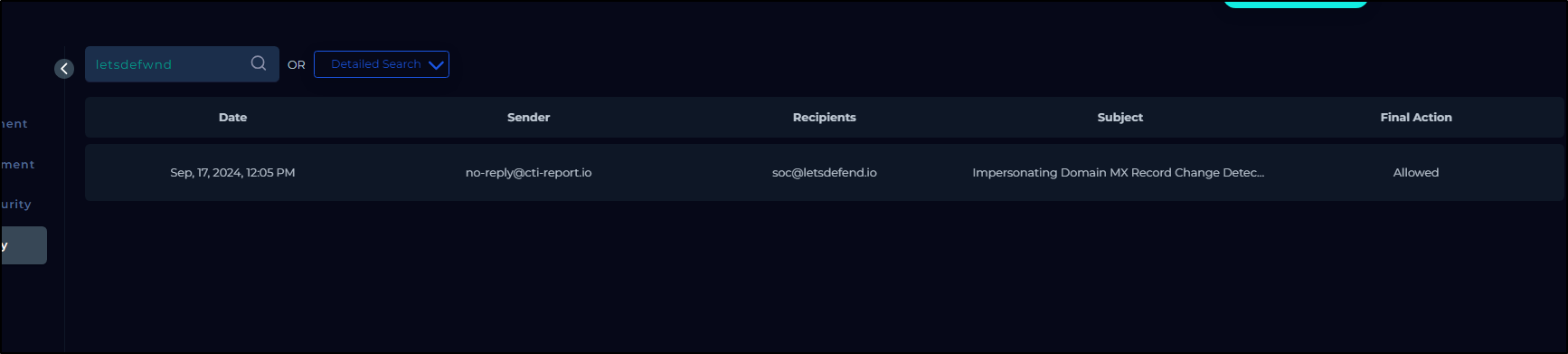
Here, we can look for the malicious domain in question letsdwfend.io
We see only one alert, and it comes from the notification in question
This email notification outlines the findings that we discussed earlier, providing a bit more detail such as the domain registrar & registrant
Let’s search letsdefwnd.io against VirusTotals database
As we can see, the domain is flagged as a phishing domain
Let’s create a playbook for this alert as necessary
Playbook Questions
Are there any or URLs in the email?
- Technically, yes. However, it wasn’t a phishing email as it was the notification email
Analyze Url/Attachment
- The domain
letsdefwnd.iowas searched via VirusTotal
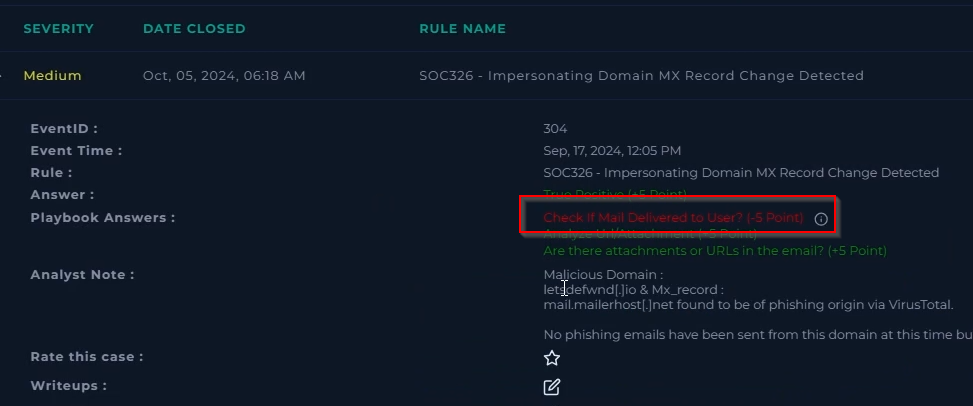
Check if Mail Delivered to User?
- I answered no here, (this is incorrect) since no actual phishing email was sent
Delete Email from recipient!
- Nothing to delete outside of an alert
Containment
- Nothing to contain
Artifacts
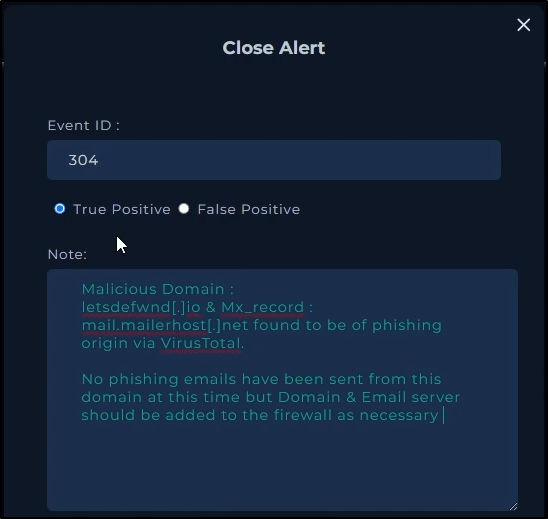
Analyst Note
Results
As we can see, I got the check if mail delivered to user question incorrect. I’m unsure if the notification email constituted as a yes to this question or not as I could not find an actual phishing email that was sent from the typosquatted email in question
Feel free to send me a message on YouTube / Linkdin if I got something incorrect
GG, thats SOC326!