1337 Corp Investigation
Investigating 1337 Corp Logs
Determining atypical activity
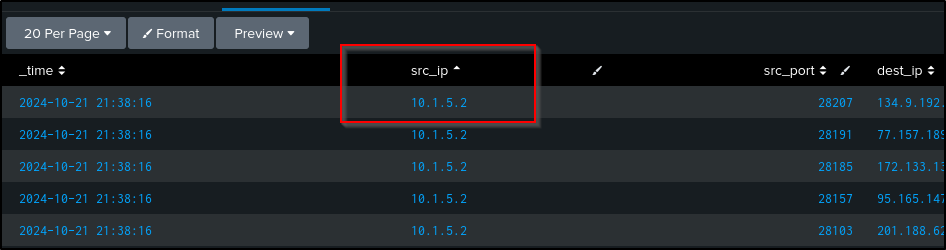
First, let’s determine if there’s any external IP addresses attempting to communicate with the system
index=* source="1337CorpFirewall[1][1][1].csv"
| table _time, src_ip, src_port, dest_ip, dest_port, bytes_in, bytes_out
We’ll will pipe our results to the table command for betting formatting while searching for relevant information
All IP addresses coming from src-ip to the firewall are private IP addresses. This confirms there are no external IPs attempting to communicate with the firewall provided by the firewall log that was given
Discovering brute-force / Failed Logon
First I’ll try to find any failed login attempts
index=* source="1337CorpADServer[1][1][1].csv" | search "login" OR "authentication" OR "logged" OR "failed" | table _time, user, src_ip
Unable to find any failed logins, let’s look for logins within a short time period
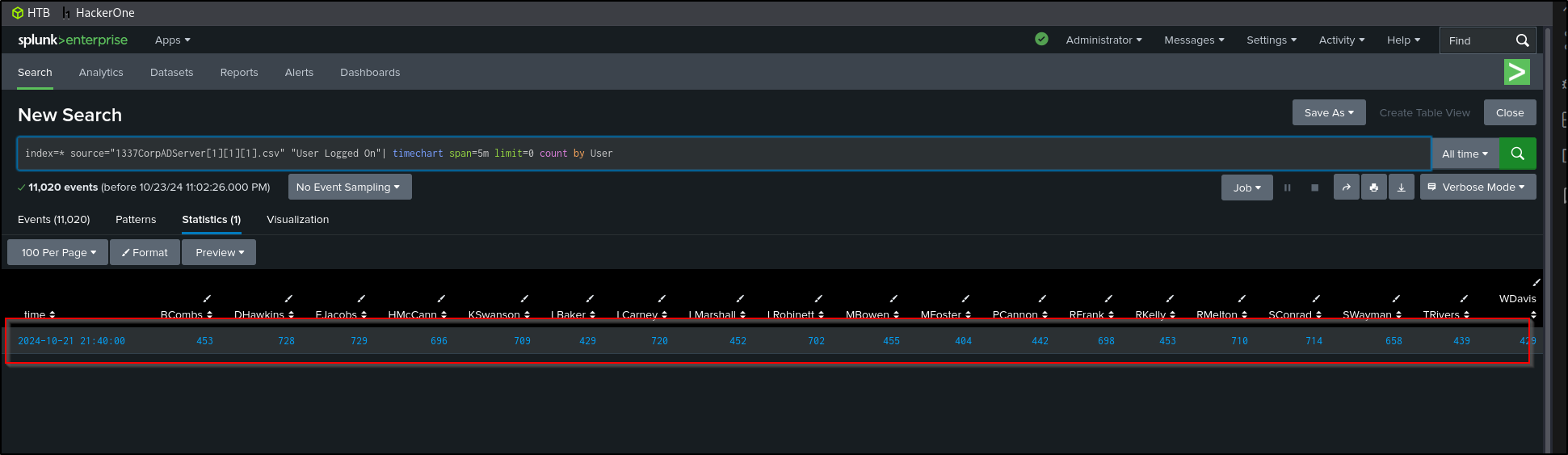
index=* source="1337CorpADServer[1][1][1].csv" "User Logged On"
| timechart span=5m count by User
We see that all 19 users have hundreds of logins, and all logins occurred exactly at the same time 9:44 PM on 10/21/2024
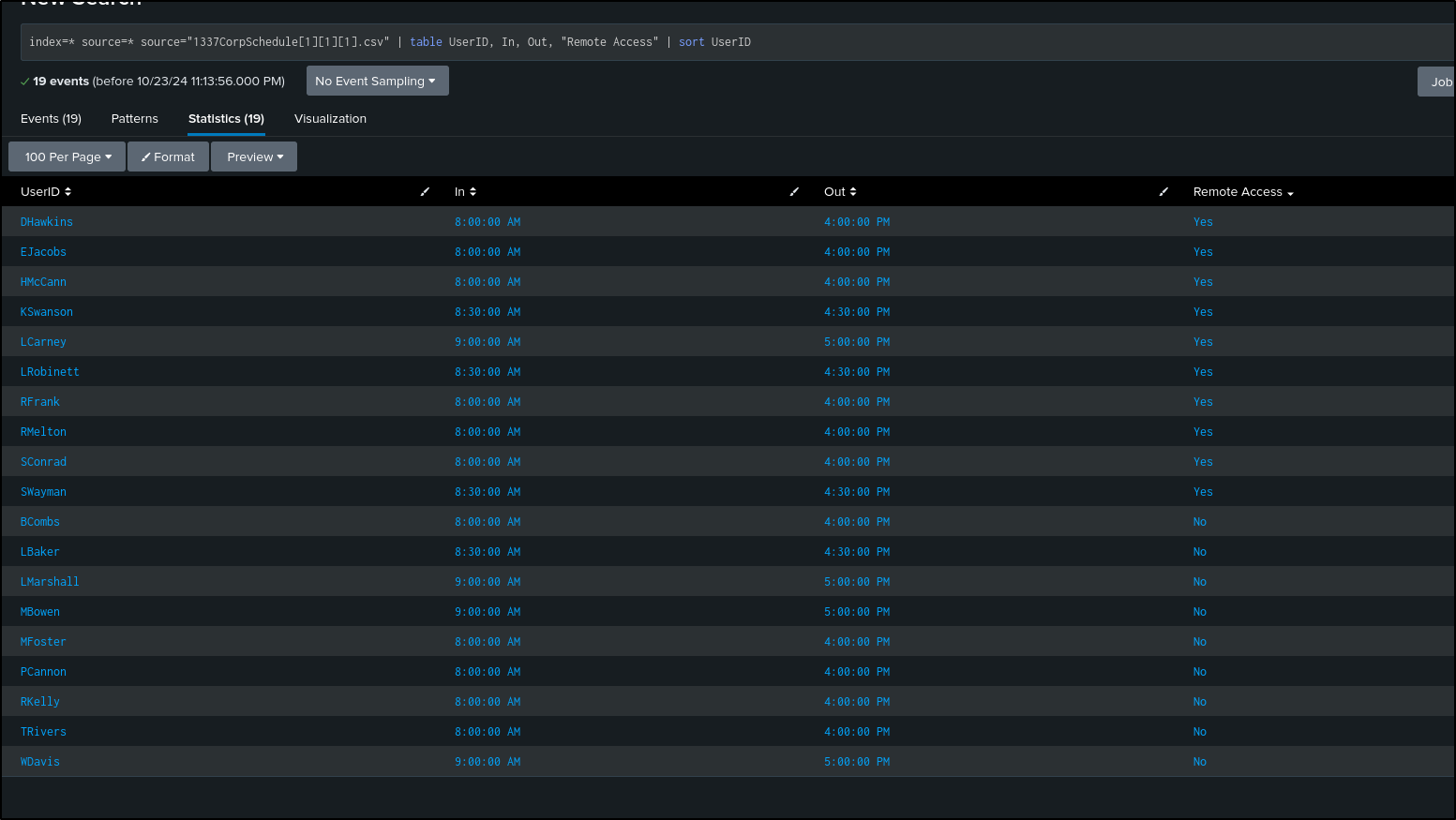
index=* source="1337CorpSchedule[1][1][1].csv" | table UserID, In, Out, "Remote Access" | sort UserID
Looking at our schedule, only 10 of the users have remote access, and NONE are in after 5:00pm
This suggests there might be a script running for some sort of automation task. Let’s check the system logs.
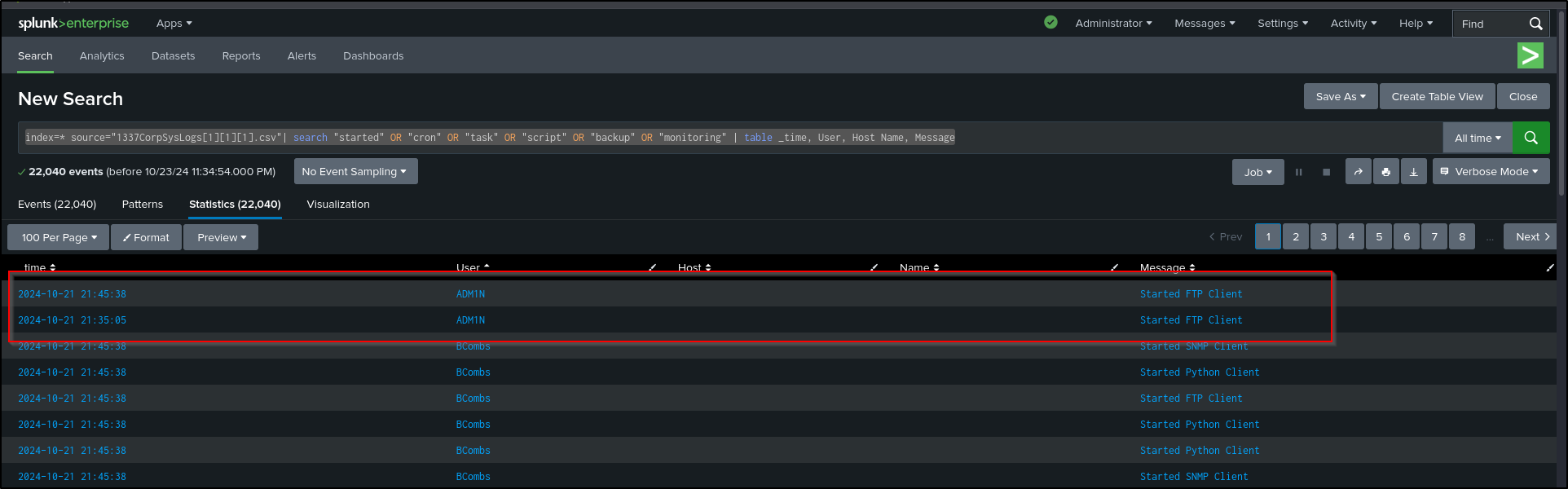
index=* source="1337CorpSysLogs[1][1][1].csv"| search "started" OR "cron" OR "task" OR "script" OR "backup" OR "monitoring" | table _time, User, Host Name, Message
The system logs show that a user by the name of ADM1N started an FTP client at 9:35 PM & 9:45 PM which is very close to the login spike from earlier
This suggest that this account has something to with data transfers
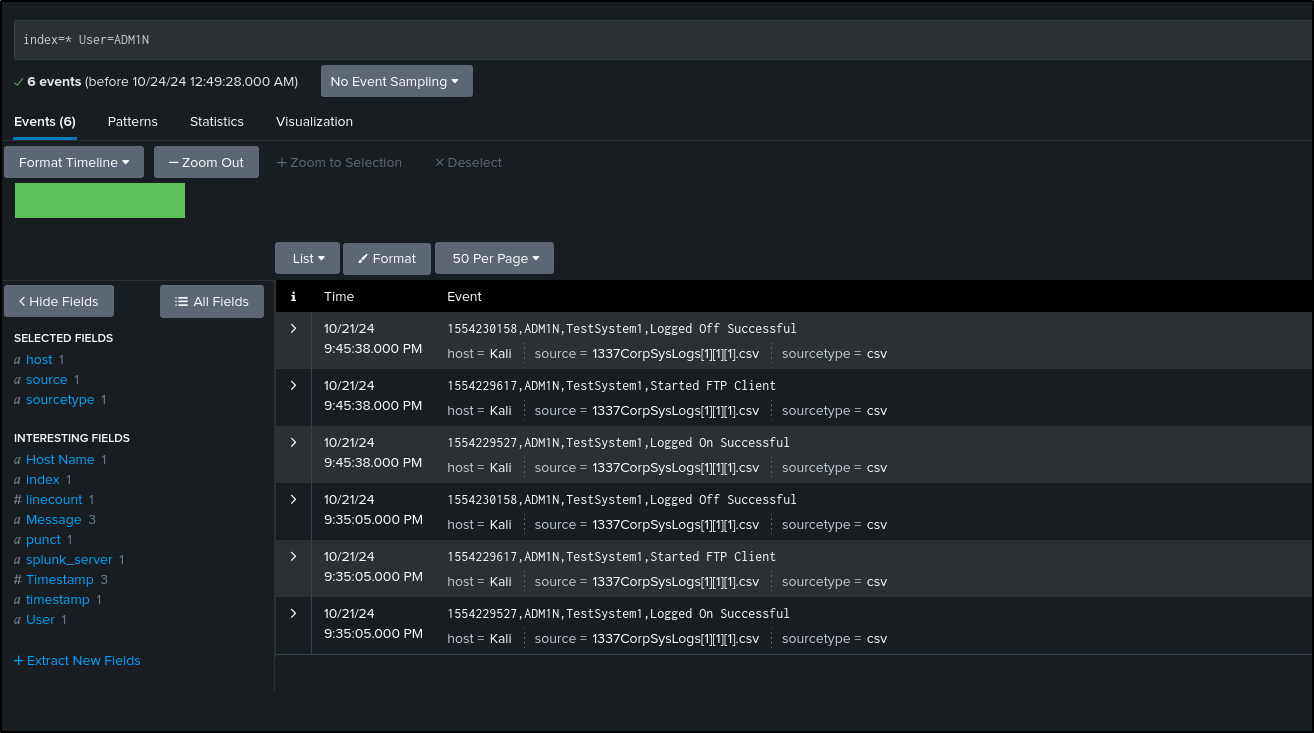
Let’s looking into this ADM1N user further
We see a sequence of events (log on, start FTP, log off), on TestSystem which suggests that ADM1N might be running a script to automate file transfers or data synchronization
Checking if this is malicious
Here I’m going to search for FTP data that was sent during the time frame of the logins from earlier
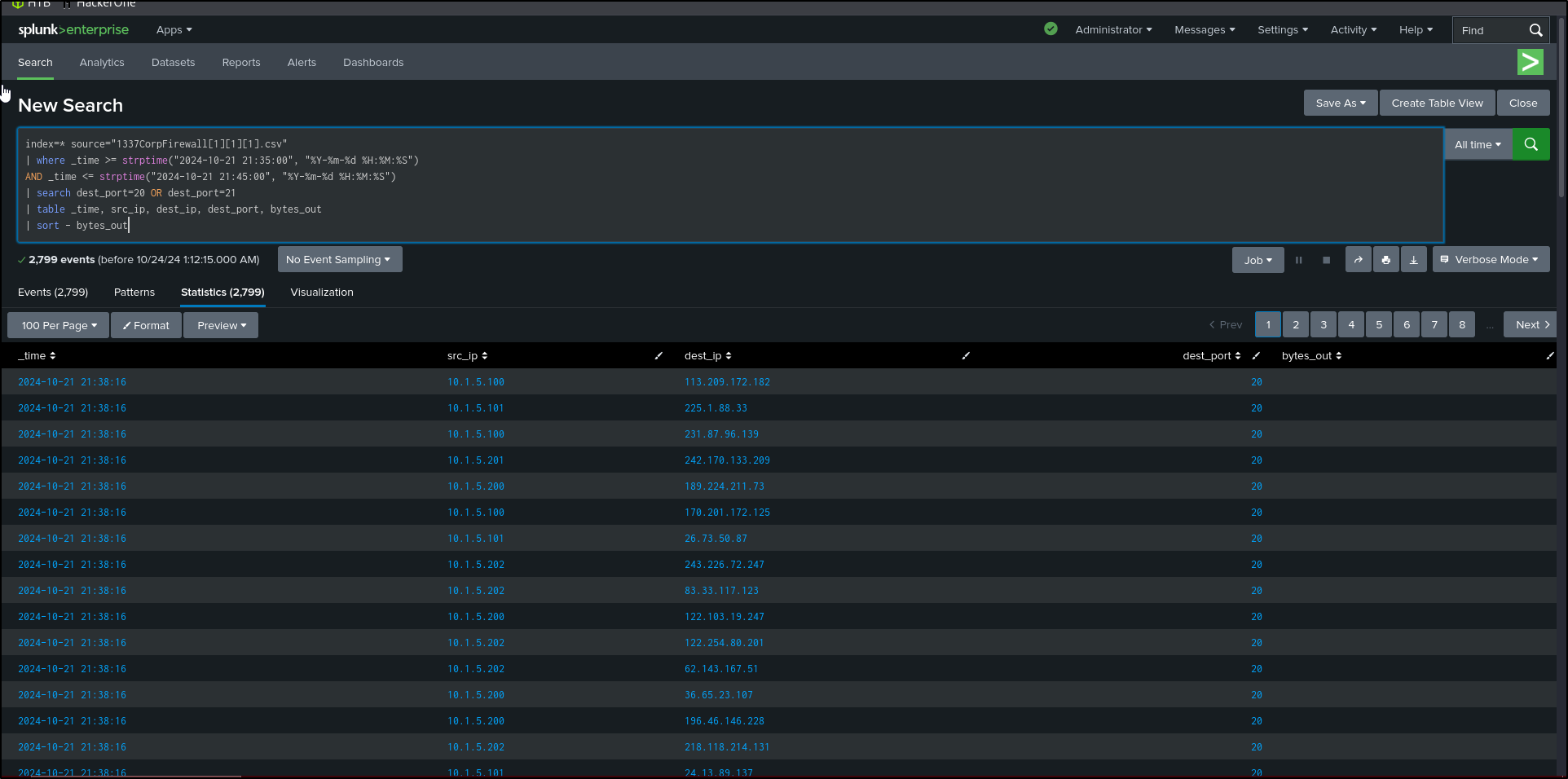
index=* source="1337CorpFirewall[1][1][1].csv"
| where _time >= strptime("2024-10-21 21:35:00", "%Y-%m-%d %H:%M:%S")
AND _time <= strptime("2024-10-21 21:45:00", "%Y-%m-%d %H:%M:%S")
| search dest_port=20 OR dest_port=21
| table _time, src_ip, dest_ip, dest_port, bytes_out
| sort - bytes_out
Our query shows many connections via FTP to external IP addresses, suggesting malicious outbound data transfer
Let’s gather all unique external IP addresses during this time
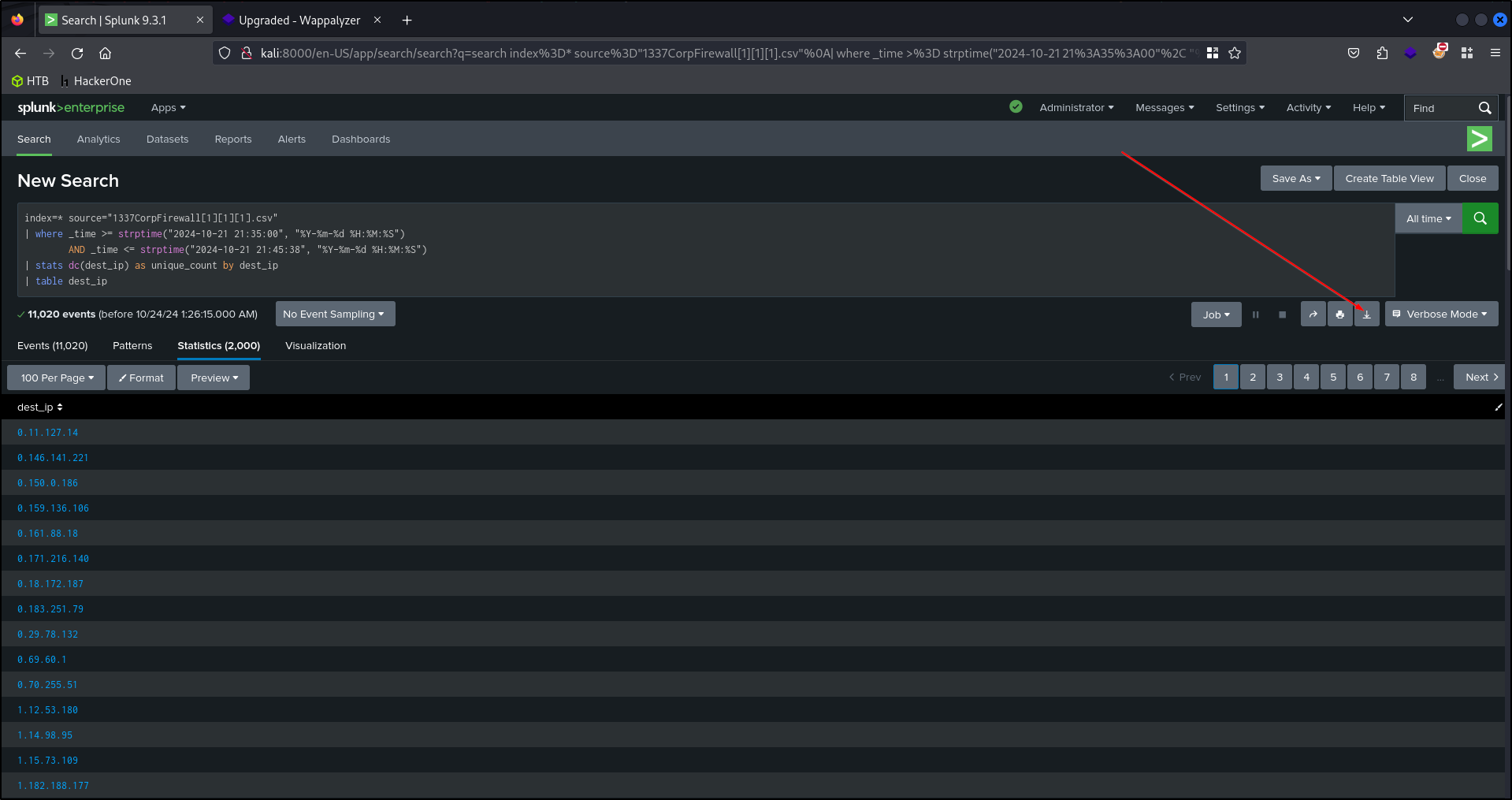
index=* source="1337CorpFirewall[1][1][1].csv"
| where _time >= strptime("2024-10-21 21:35:00", "%Y-%m-%d %H:%M:%S")
AND _time <= strptime("2024-10-21 21:45:38", "%Y-%m-%d %H:%M:%S")
| stats dc(dest_ip) as unique_count by dest_ip
| table dest_ip
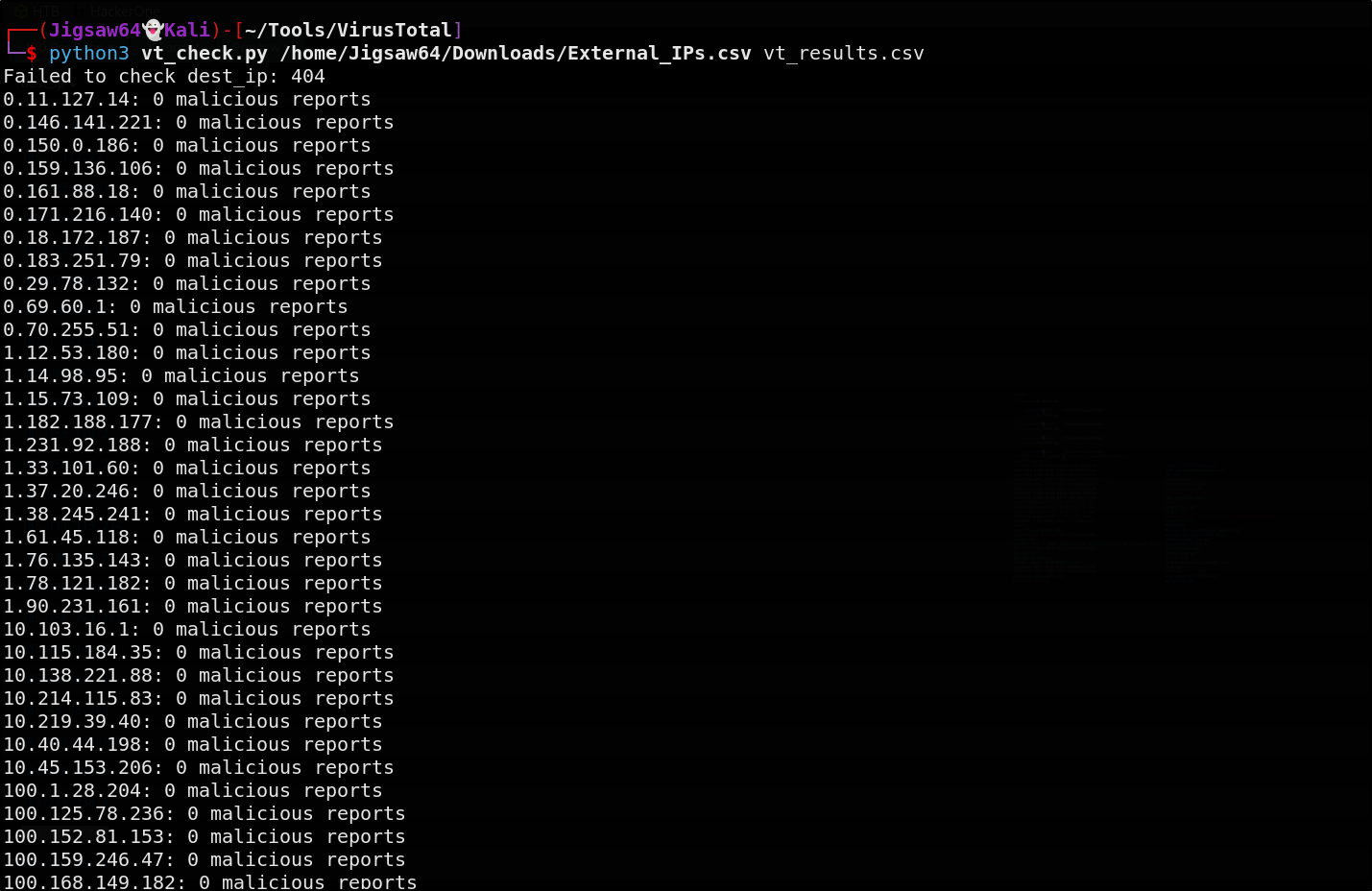
After downloading the CSV file, we can run it against a python script using the VirusTotal API
Unfortunately, I am rate limited on the free version of the API. However, we don’t see any malicious reports
Conclusion
- Mass user logins at 9:44 - outside of scheduled working hours
- FTP transfers from all users immediately after logins
- The ADM1N account initiating FTP activity before and after these events
- No malicious reports on these IPs
Reasonable explanations
- Unauthorized data exfiltration by insider threat or compromised ADM1N account after hours (most likely)
- Legitimate automated backup traffic (less likely)
Next steps
- Investigate the data that was transferred
- Audit the ADM1N account / user